The attacks disclosed recently by Twilio and Cloudflare were part of a massive phishing campaign that targeted at least 130 other organizations, according to cybersecurity company Group-IB.
Enterprise communications firm Twilio and web security company Cloudflare reported earlier this month that their employees had fallen for SMS-based phishing messages whose goal was to trick them into handing over their credentials.
Twilio said the attackers were successful in obtaining employee credentials, which they used to access internal systems and customer data. In an update shared on August 24, Twilio said the incident impacted 163 of its 270,000 customers, as well as 93 of the 75 million individual Authy users.
Authy is Twilio’s two-factor authentication (2FA) solution and the attackers registered additional devices to the compromised Authy accounts.
Secure communications firm Signal was one of the impacted Twilio customers. The company said 1,900 of its users were impacted by the incident, with the attackers attempting to re-register these users’ phone numbers to new devices.
Cloudflare admitted that some of its employees fell for the phishing attempts, but said the attackers could not get past 2FA, which leverages physical security keys.
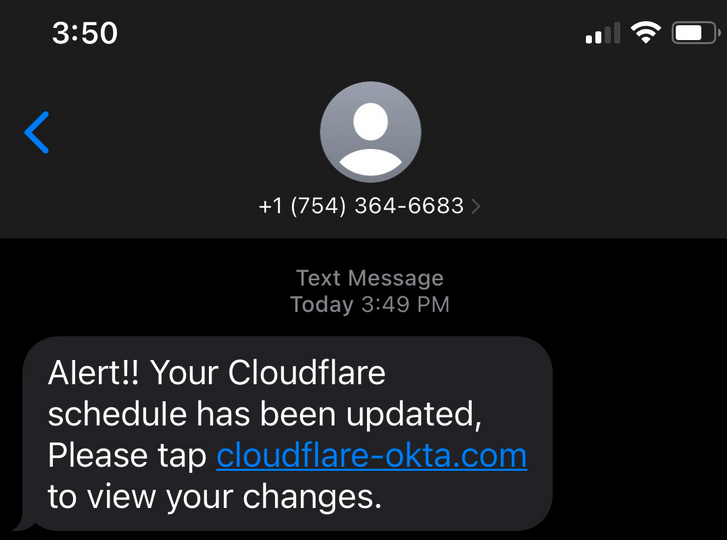
According to Group-IB, these attacks were part of a massive phishing campaign that has been active since at least March 2022. The company said on Thursday that the attackers have managed to compromise nearly 10,000 accounts at more than 130 organizations.
The campaign is tracked by Group-IB as 0ktapus — the name is related to the attackers mainly targeting Okta identity service credentials. In addition to Okta credentials, they were looking to obtain 2FA codes.
The hackers sent out phishing SMS messages to the target’s employees in an effort to lure them to fake Okta login pages. Once the credentials were harvested, they would be used by the threat actor to access internal systems and sensitive customer data.
Group-IB says it’s unclear how the employee phone numbers were obtained, but it believes the attackers also targeted mobile operators and telecoms companies to achieve this goal.
The stolen data is sent by the phishing pages to a Telegram channel controlled by the attacker. On this channel, researchers discovered 9,931 credentials, including 3,129 records with emails and 5,441 with 2FA codes.
An analysis of the data revealed 136 victim organizations, including 114 in the United States. The other victims appear to be spread out across tens of other countries. Many victims are in the software, telecom, business services, and finance sectors.
“Seeing financial companies in the compromised list gives us the idea that the attackers were also trying to steal money. Furthermore, some of the targeted companies provide access to crypto assets and markets, whereas others develop investment tools,” Group-IB said in a blog post.
“Based on recent news about hacked Signal accounts, we can assume the fraudsters may try to get access to private conversations and data. That information can be used as business intelligence and reselled to the victim’s competitors or could be used to ransom a victim,” it added.
Group-IB suggested that recently disclosed breaches at marketing companies Mailchimp and Klaviyo were part of supply chain attacks that were subsequently launched as part of the 0ktapus campaign.
The cybersecurity firm has also looked at clues pointing to the identity of the threat actor, which led them to an individual whose social media accounts suggested he was based in the US, specifically North Carolina. The identity of the individual has not been made public, but Group-IB has been known to have helped authorities identify cybercriminals so it’s likely that the company has shared its findings with law enforcement.
Related: Cryptocurrency Services Hit by Data Breach at CRM Company HubSpot
Related: Microsoft, Okta Confirm Data Breaches Involving Compromised Accounts














