A mysterious cybercrime group apparently driven by profit has been targeting industrial organizations in Europe, Asia and North America as part of an information theft campaign.
The campaign was detailed in September 2020 by cybersecurity firm Zscaler, which warned at the time that the hackers had been targeting oil and gas supply chain industries in the Middle East using the trojan known as AZORult.
These attacks are ongoing, according to DeNexus, a California-based provider of cyber risk modeling for industrial networks, which on Thursday published a report detailing this campaign, its evolution, and additional victims.
DeNexus reported seeing targets and victims in various countries, and noted that in addition to AZORult, the attackers have been spotted using information-stealing malware such as AgentTesla, Formbook, Masslogger and Matiex.
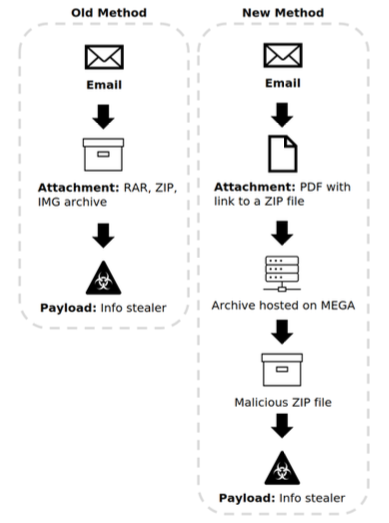
The malware is delivered using spear phishing emails that purport to come from legitimate companies, including from within the victim organization itself and other companies that the victim might do business with. In more recent attacks, the cybercriminals have put more effort into these emails, including by registering domains with names similar to the one of the targeted firm.
While the hackers appear to be mainly interested in oil and gas supply chain industries in the Middle East, they have also been seen targeting other types of organizations in other regions.
Learn More About Threats to Industrial Systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits Virtual Event Series
DeNexus said the list of targeted European companies includes a commercial refrigerator supplier, a provider of heavy electrotechnical equipment, a manufacturer of optical components, and a smart automation solutions provider. In the APAC region, the threat group targeted an industrial process and factory automation firm, a construction materials manufacturer, and a transportation services company. In the Middle East, they also targeted international maritime organizations and in North America a US-based manufacturer of anti-slip covers.
The list of organizations whose employees did install the threat actor’s malware includes an aerospace company in India, and development company in South Korea, a services provider for the oil and gas industry in the UAE, a logistics and transportation company in the UAE, the national oil and gas company of Sri Lanka, an oil and gas company in China, and a petrochemical and textile firm in China.
Vladimir Dashchenko, VP of threat intelligence at DeNexus, told SecurityWeek that since Zscaler published its report on this operation, the threat actor has taken steps to increase chances of avoiding detection (e.g. hosting malware on cloud services), and it has started using the compromised companies’ email accounts as command and control (C&C) servers.
The researcher said that this appears to be a profit-driven group rather than a state-sponsored threat actor. It’s also worth mentioning that it has not been seen targeting industrial devices, protocols or processes. While they are currently focusing on stealing information, once they have gained initial access to an organization’s IT network, they could at any time try to move to operational technology (OT) networks as well, Dashchenko said.
The threat actor is likely still active — DeNexus last observed activity on February 9, but says it continues to monitor the campaign.
Antivirus company Bitdefender also published a report last year to describe attacks on oil and gas organizations, and those attacks also involved the AgentTesla malware, but DeNexus does not believe they are related.
Related: Hundreds of Industrial Organizations Received Sunburst Malware in SolarWinds Attack
Related: Number of ICS Vulnerabilities Continued to Increase in 2020: Report
Related: Industrial Suppliers in Japan, Europe Targeted in Sophisticated Attacks















