Cyber Espionage Attacks Hit Philippine Oil Company and Canadian Energy Firm
Researchers from Dell SecureWorks’ Counter Threat Unit say they have discovered yet another cyber espionage campaign targeting oil and energy companies.
Its targets, they say, include a large oil company in the Philippines, an energy company in Canada, a military organization in Taiwan and other organizations in Brazil, Israel, Egypt and Nigeria.
“Based on the data collected by the CTU research team, the campaign’s primary attack vector is spearphishing email that targets mid-level to senior-level executives,” blogged Silas Cutler of Dell SecureWorks Counter Threat Unit, Threat Intelligence. “These emails contain an attachment that includes a malicious payload that installs a copy of Mirage.”
The “weaponized” attachments are designed to look like PDF files but are actually “droppers” – standalone executable files that open an embedded PDF file an execute Mirage, Cutler explained.
To get a better understanding of the attack, the company’s research team launched a sinkhole operation in May. As a result, CTU researchers were able to identify roughly 80 IP addresses regularly communicating with the sinkhole. After decoding the inbound requests, the team identified between 100-120 infected systems attempting to phone home.
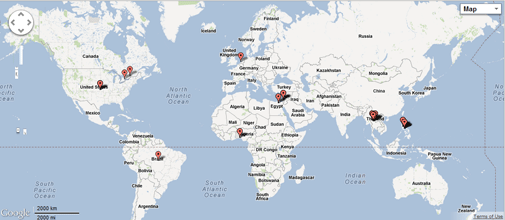
Figure 1 – Source of Infected Hosts (Courtesy of Dell SecureWorks)
“The threat actors using Mirage have employed several tactics to attempt to hide their identities and their primary C2 (command-and-control) servers,” Cutler blogged. “One of the common tactics is using dynamic domain name system (dDNS) domains for the callbacks to the C2 servers. dDNS providers (e.g., Dyndns.com) allow anyone to register for a free third-level domain (e.g., Checkip.dyndns.org) and require only a valid email address, which is kept private.”
While investigating the DNS addresses of the command and control servers, researchers identified several IP addresses of hosting companies based in the United States that are running HTran, which is used to proxy connections from one system to another. Previously, CTU analysis identified the author of HTran as a member of the Chinese hacker group HUC, the Honker Union of China.
“Despite efforts to operate anonymously, there were several clues that pointed to the true identities of the attackers,” Cutler blogged. “During an analysis of the phone-home activity, CTU researchers identified four unique second-level domains that were not connected to a dDNS provider. Two of these domains shared a common owner’s email address, and two were previously flagged for suspicious activity.”
Further analysis revealed that the command and control IP addresses belonged to the China Unicom Beijing Province Network.
“Mirage represents only one small piece of malware involved in an ongoing worldwide campaign,” Cutler noted. “Over the past few years, these campaigns have become extremely successful, and a great deal of intellectual property and company secrets has been stolen from the targeted companies.”
Additional details on the Mirage Campaign can be found here.














