Whistleblower site Cryptome has been hacked and infected by the Blackhole exploit kit.
Just how the breach occurred has not been said. Cryptome co-founder John Young however told SecurityWeek that the site is in the process of cleaning everything up, and that process should be finished by the end of the day.
“It appears every HTML page was infected so we are replacing all the pages to be sure,” he said.
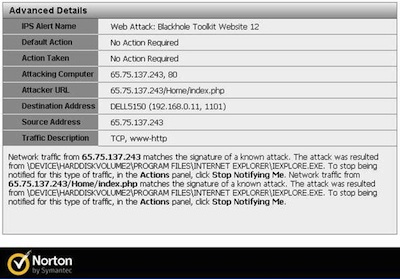 Founded in 1996, Cryptome publishes thousands of documents, including many related to national security, law enforcement and military. On Feb. 12, a reader advised the site that accessing a file had triggered a warning in their antivirus about the Blackhole exploit kit. Cryptome examined the file and found this command at its end: < SCRIPT src=”/0002/afg/afg.php”>. Subsequent analysis found thousands of files on the site had been infected.
Founded in 1996, Cryptome publishes thousands of documents, including many related to national security, law enforcement and military. On Feb. 12, a reader advised the site that accessing a file had triggered a warning in their antivirus about the Blackhole exploit kit. Cryptome examined the file and found this command at its end: < SCRIPT src=”/0002/afg/afg.php”>. Subsequent analysis found thousands of files on the site had been infected.
Blackhole has emerged as one of the most prevalent exploit kits in the wild. In a recent report, M86 Security said the Blackhole kit was responsible for 95 percent of all the malicious URLs detected by M86 in the second half of 2011.
“One of the significant advantages of the Blackhole exploit kit over its competitors is the frequency of updating,” according to the report. “For example, the vulnerability, CVE-2011-3544 Oracle Java Applet Rhino Script Engine Remote Code Execution, a zero-day that was published at the end of November, was exploited a few days later in the wild by the Blackhole exploit kit.”
That a reader notified the site of the problem is in keeping with a recent finding from Trustwave, which reported that of the data breaches they investigated in 2011, only 16 percent of the victimized organizations were able to detect the breach themselves.















