Cloud Security Study: IT Unaware of All Cloud Services Used in Their Enterprise; Less Than Half of are Properly Evaluated for Security
Cloud computing is proving to be an important trend in information technology globally. The benefits for business and IT include cost reduction, increased productivity, and scalability. Unfortunately, many organizations are migrating to the cloud without ensuring the data they put in the cloud is secure.
CA, Inc. (NASDAQ: CA) and the Ponemon Institute, today announced the results of a recent study analyzing the security concerns of IT professionals surrounding the utilization of cloud services within their organization.
The study, entitled “Security of Cloud Computing Users,” showed that over half of U.S. organizations are adopting cloud services, but only 47 percent of respondents say that cloud services are properly evaluated for security prior to deployment. Additionally, more than 50 percent of respondents in the U.S. say they are unaware of all the cloud services currently in use in within their enterprise.
Some key discoveries showed substantial concern across industries in maintaining security for mission critical data and business processes in the cloud. IT practitioners noted that a variety of data sets were still too risky to move to the cloud:
- 68 percent thought that cloud computing was too risky to store financial information and intellectual property;
- 55 percent did not want to store health records in the cloud; and
- 43 percent were not in favor of storing credit card information in the cloud.
Additional key findings from the study included:
- Less than 30 percent of respondents were confident they could control privileged user access to sensitive data in the cloud.
- Only 14 percent of respondents believe cloud computing would actually improve their organization’s security posture.
- Just 38 percent of respondents agreed that their organization had identified information deemed too sensitive to be stored in the cloud.
The results demonstrate that IT managers need to take a full inventory of their organization’s cloud computing resources, closely evaluate cloud providers, and properly assess the risks with putting customer and company data in the cloud. IT managers also need to implement policies around what data is appropriate for cloud use and evaluate deployments before they are made.
“Organizations need to ensure the cloud – whether you’re talking about applications, platforms or infrastructure – is secure before they use it. The study results indicate that organizations are approaching cloud security differently than they do enterprise security and not applying the same best practices and policies they use for the enterprise,” said Lina Liberti, vice president of product marketing, CA Security.
While cloud computing services can offer cost savings and efficiencies to many organizations, evaluating and implementing the security practices may offset some of the benefits, diminishing one of the main reasons for choosing the cloud. Despite such concerns, the data suggests that many organizations will pay a premium to cloud providers that prove to be secure.
“Organizations need to extend their security policies to accommodate the cloud and should look for security transparency from their providers.” “Organizations put themselves at risk if they fail to evaluate cloud services for security and don’t have a view of what cloud services are in use throughout the business,” said Dave Hansen, corporate senior vice president and general manager for CA’s Security business unit. “All parties – IT, the end user, and management – should be involved in the decision making process, and need to build guidance around cloud computing adoption to help their organizations more securely deploy cloud services.”
The Security of Cloud Computing Users study sampled 642 IT and IT security practitioners in the U.S. with an average of 12 years experience in the field. The study was conducted during the month of March, and included both technicians and managers in a wide range of industries.
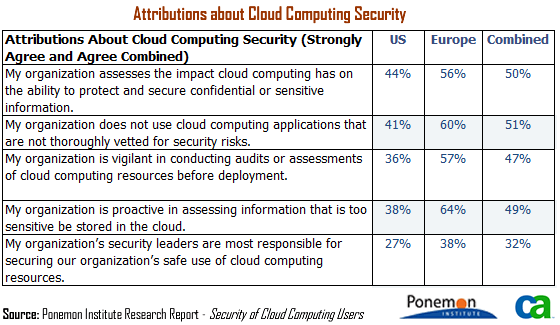
The table below reports five attributes concerning respondents’ views about the security of cloud computing within their organizations.
In the coming months, CA, Inc. and The Ponemon Institute plan to release the results of second study focused on cloud computing providers located in the United States and Europe.













