The Chinese APT known as TA423 (aka Red Ladon, APT40 and Leviathan) has been operating a cyberespionage campaign across Australia, Malaysia and Europe. The campaign has had three distinct phases – the latest from April 2022 to mid-June 2022. The primary targets have been Australian organizations and energy exploration in the South China Sea.
TA423 has been active since 2013, with previous targets including defense contractors, manufacturers, universities, government agencies, legal firms involved in diplomatic disputes, and foreign companies involved with Australasian policy or South China Sea operations. The focus is on areas of geopolitical interest to the Chinese government.
In July 2021, the US government indicted four Chinese nationals (three of whom it said were provincial officers in China’s Ministry of State Security) for APT40-related cyberespionage.
The latest operation, reported by Proofpoint with assistance from PwC, involved phishing campaigns designed to lure victims to a malicious website designed as an Australian news site. The site delivered the ScanBox reconnaissance and exploitation framework first analyzed by AlienVault in 2014, and believed to be used by several different Chinese threat groups.
Targets received messages from email addresses created by the threat actor asking the recipient to visit a false website for the fictional Australian Morning News. The site used genuine news stories lifted from sources such as Reuters and the BBC. Targets who visited the website were served with ScanBox.
ScanBox delivers JavaScript code either as a single block or, as here, as a plugin-based modular architecture. The primary payload sets its configuration including the information to be gathered, and the C2 server to be contacted. It harvests detailed data on the browser being used.
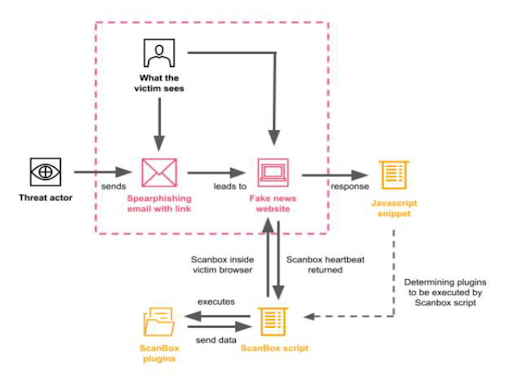
Infection chain and ScanBox control flow
Subsequent ScanBox plugins delivered to the victim include a keylogger, browser plugin identification, browser fingerprinting, a peer connection plugin (avoiding the need to communicate through NATs, firewalls and other security solutions), and a security check for Kaspersky Internet Security (KIS).
The latest campaign is phase 3 of an ongoing campaign primarily targeting Australia and Malaysia. From March 2021, Proofpoint observed focused TA423 targeting these countries and offshore energy firms. At that time (phase 1) the phishing campaign involved weaponized RTF attachments that ultimately retrieved versions of Meterpreter shellcode.
The Australian targets included military academic institutions, and federal government, defense and public health sectors. The Malaysian targets included offshore drilling and deep-water energy exploration firms, and global marketing and finance companies. Other global companies targeted may have been part of the supply chain for the energy firms.
Phase 2 occurred in March 2022. It used RTF template injection attachments which returned a macro-laden Microsoft Word document. Although Proofpoint has not yet been able to retrieve the payload, observation of similar weaponized RTF files suggests the delivery of a DLL downloader that delivers an XOR encoded Meterpreter payload response.
The latest campaign, phase 3, is effectively a phishing/watering hole campaign that delivers a customized version of ScanBox.
The three phases are considered by Proofpoint and PwC threat analysts to be part of a continuous and ongoing sustained phishing campaign targeting Malaysia and Australia and attributed to TA423 (APT40). The attacks appear to be directed against targets of strategic importance to China in a time of heightened geopolitical tensions.
TA423 is thought to operate out of China’s Hainan Island in the South China Sea – the most southern point of China, The US government indictment of four Chinese nationals linked the group to the Chinese Hainan Province Ministry of State Security. However, the indictment appears to have had no effect on the operations of the group. Both Proofpoint and PwC expect TA423 (APT 40) to continue its espionage activities targeting countries in the South China Sea, and further intrusions in Australia, Europe and the US.
Related: State-Sponsored Hackers Supporting China’s Naval Modernization Efforts
Related: China-linked Hackers Target Engineering and Maritime Industries
Related: Microsoft Says China-Linked Hackers Abused Azure in Attacks















