News Analysis: Cybersecurity experts toss bouquets at Apple for removing attack surface from its flagship platforms and call on competing OS makers to match Cupertino’s attempts to neutralize the mercenary spyware business.
Apple’s decision to architect a new operating system ‘Lockdown Mode’ to counteract the mercenary spyware exploitation business is receiving rave reviews from cybersecurity experts monitoring the software surveillance landscape.
“Let me say, right out of the gate, this is great,” says Claudio Guarnieri, head of the Security Lab at Amnesty International. “This is responsible and mindful engineering.”
Guarnieri, who works on documenting infections by surveillance software products, said the stripped-down versions of iPhones, iPads and macOS-powered devices will “raise the economic costs for attackers” and help to neutralize some the most technically sophisticated exploits ever seen.
According to Apple, the new Lockdown Mode will be an extreme, optional OS version for a tiny percentage of its users who are targeted with sophisticated exploits capable of silently infecting iPhones without the user clicking on malicious links or surfing to rigged websites.
Security researchers at Google’s Project Zero have described one of the iOS zero-click exploits as “a weapon against which there is no defense” and made it clear that “there is no way to prevent exploitation by a zero-click exploit.”
With Lockdown Mode, currently in beta and expected to ship in the fall, Apple is betting that the removal of certain features and functionalities will provide technical roadblocks to the zero-click exploits that dominate global news headlines.
[ Read: Google: Pegasus Zero-Click ‘Most Technically Sophisticated Exploit Ever Seen’ ]
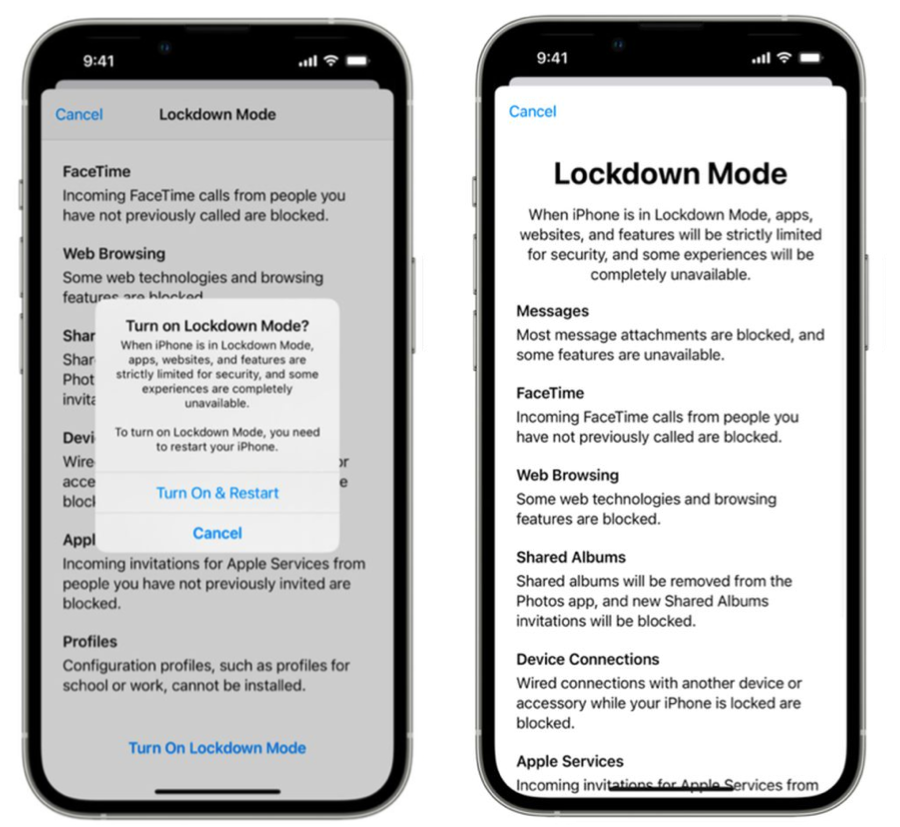
For example, the popular default Messages app will be modified to block some message attachment types and disable link previews. This change, while limiting functionality, effectively neutralizes software exploits that use Message attachments as the initial delivery mechanism.
“Message attachments can be a first point of entry in potential exploitation chains. Vulnerabilities often occur in complex file format parsers, which are perfect attack vectors and as a result they are a preferred target for offensive security researchers’ fuzzing and reverse engineering efforts,” Guarnieri said.
Apple is well aware of these types of exploits, having patched multiple zero-day exploits linked to surveillance software makers over the last two years. One of those exploits, called FORCEDENTRY, exploited a flaw in the way the Messages app previewed images to infect target devices.
By reducing the allowed message attachment types, Amnesty International Guarnieri says Apple is reducing a major, known attack surface and the efforts may allow Cupertino’s security engineers to prioritize auditing efforts.
[ Read: Apple Adds ‘BlastDoor’ to Secure iPhones From Zero-Click Attacks ]
Apple’s software engineers also plan to block incoming invitations and service requests, including FaceTime calls, if the user has not previously sent the initiator a call or request. This will reduce exposure to known exploitation vectors via FaceTime call requests.
In addition, complex web technologies, like just-in-time (JIT) JavaScript compilation, will be disabled unless the user excludes a trusted site from Lockdown Mode.
The mode will also block the installation of configuration profiles and disable enrollment into mobile device management (MDM) systems.
Security researchers interviewed by SecurityWeek acknowledge that Lockdown Mode will offer significant protection for journalists, political activists and dissidents targeted by nation-state spyware and applauded Apple for working on the mitigations, at the expense of widely used default features.
Still, some argue that Apple can go a step further and provide tools to help researchers inspect devices for signs of infections.
[ Read: Apple Slaps Lawsuit on NSO Group Over Pegasus iOS Exploitation ]
“The ‘features’ of Lockdown mode are all aimed at infection vectors. It’s a fixation on ever renewing ‘vulnerabilities’ rather than a lack of verifiability or inspection,” says Juan Andres Guerrero-Saade, principal security researcher at SentinelLabs and an adjunct lecturer at Johns Hopkins SAIS.
“Until there’s an effort to empower researchers, incident responders, and victims to defend, verify, and remediate spyware on their devices (no matter how ‘high-end’ the malware, or how ‘few people affected’), Apple’s approach to iOS security remains one of willful ignorance,” Guerrero-Saade added.
Google’s James Forshaw, a prominent Project Zero researcher, described Lockdown Mode as “interesting” but said a real game-changer would be “system transparency so you could actually inspect your iOS device without jailbreaking it.”
“After all, how can you verify Lockdown Mode hasn’t been tampered with?,” Forshaw reacted on Twitter.
Despite these reservations, Amnesty International’s Guarnieri is pleased with the progress. “Regardless of how effective Lockdown Mode will turn out to be in its first iteration, this is a critically important development from a top hardware and software manufacturer like Apple.”
“Will other manufacturers follow the example?” Guarnieri asked, echoing calls from the security research community for a similar, easy-to-use setting that limits attack surfaces on Android and other rival mobile operating systems.
Related: Apple Adds ‘Lockdown Mode’ to Thwart .Gov Mercenary Spyware
Related: Apple Adds ‘BlastDoor’ to Secure iPhones From Zero-Click Attacks
Related: Google: NSO Zero-Click ‘Most Technically Sophisticated Exploit Ever Seen’
Related: Apple Slaps Lawsuit on NSO Group Over Pegasus iOS Exploitation
Related: Secretive Israeli Exploit Company Behind Wave of Zero-Day Exploits














