The cybercriminals behind the BlackMatter Ransomware-as-a-Service (RaaS) operation this week announced plans to close shop.
Active since July 2021, BlackMatter is the product of the Coreid cybercrime group, which also operated the DarkSide ransomware. BlackMatter’s use in assaults on critical infrastructure entities in the United States has resulted in the U.S. government recently issuing an alert on the RaaS operation.
On Monday, the BlackMatter operators posted on their RaaS website a message announcing that the entire operation would be shutting down within 48 hours.
In their message, the miscreants mention increased pressure from the authorities and say that part of the team is no longer available “after the latest news,” most likely a reference to last week’s wave of arrests in Europe.
A total of 12 suspects were arrested, most of them being considered high-value targets due to their involvement in multiple high-profile cases, Europol said.
Despite operating for only four months, BlackMatter emerged as one of the most prolific ransomware operations out there, with more than 50 businesses being hit to date.
At an average ransom demand of $5.3 million, the attackers could have made hundreds of millions from the operation, but the total amount is yet unknown. In September, the cybercriminals demanded $5.9 million from Iowa-based New Cooperative.
The highest ransom demand made by the BlackMatter gang was of $30 million, requested from Japan’s Olympus Corporation, Singapore-based cybersecurity firm Group-IB says.
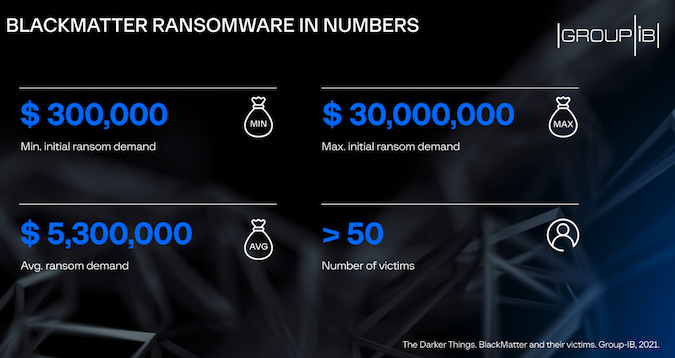
The estimates are based on the negotiation chats the cybercriminals had with their victims. Responding to a SecurityWeek inquiry, Group-IB didn’t make an estimate as to how much the BlackMatter gang might have made from the operation.
“The identified cryptocurrency wallets had no transactions as they were related to the victims who refused to pay the ransom and whose data was published on the gang’s DLS. The number of victims who actually paid the ransom as well as the gang’s earnings are unknown,” Oleg Skulkin, head of DFIR Lab at Group-IB, said.
More than half (52%) of the organizations hit by BlackMatter are from the U.S., with others located in Austria (11%), Italy (7%) and France (7%), as well as eight other countries. The production sector was affected the most, Group-IB says.
Both Windows and Linux versions of the BlackMatter ransomware were observed and earlier this week security researchers warned that the group had developed a custom data exfiltration tool to accelerate their attacks. The stolen data was being used to pressure victims into paying the ransom.
Despite the shutdown announcement, however, security researchers believe that the gang won’t retire completely. In fact, several security experts have told SecurityWeek that BlackMatter will likely return under a different name, just as DarkSide did.
They also warn that some of the group’s members might join active RaaS operations out there and encourage organizations to strengthen their defenses against ransomware and other malicious attacks.
“This is highly unlikely to be the end of the threat actors behind the BlackMatter group and this looks like a classic rebrand or splintering. Organisations must recognise this threat and invest in their cybersecurity and help to alleviate the risk of ransomware,” Carl Wearn, head of e-crime at Mimecast, said.
Related: U.S. Government Issues Urgent Warning on BlackMatter Ransomware
Related: 12 People Arrested Over Ransomware Attacks on Critical Infrastructure















