Apple on Wednesday unveiled PQ3, a new post-quantum cryptographic protocol for iMessage that is designed to protect encrypted communications even against future quantum computing attacks.
End-to-end encryption is present by default in many popular messaging applications, but the actual level of protection depends on the cryptographic protocols they use and how they are implemented.
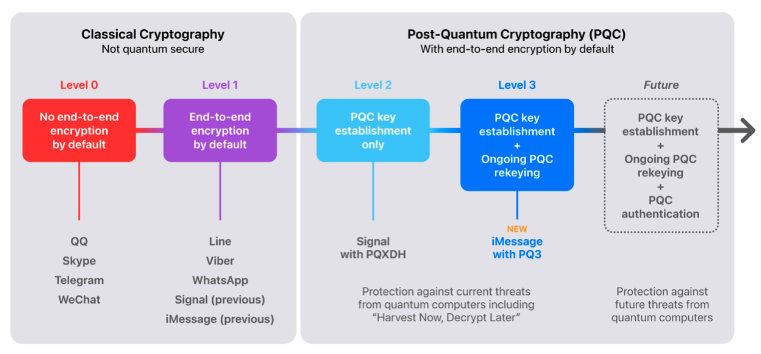
Apple describes three levels of encryption in messaging apps: level 0, apps that don’t provide end-to-end encryption by default; level 1, apps that provide end-to-end encryption by default via traditional cryptography; level 2, apps that provide post-quantum security in the initial encryption key establishment; and level 3, apps that provide post-quantum security in both key establishment and ongoing message exchanges.
The privacy-focused application Signal recently reached ‘level 2’, when it announced support for the Post-Quantum Extended Diffie-Hellman (PQXDH) protocol, but Apple says the PQ3 protocol puts iMessage in ‘level 3’, ensuring that communications are protected even if an encryption key is compromised.
The tech giant says iMessage will be the only messaging application that limits the number of past and future messages that can be decrypted by an attacker who has obtained a single encryption key. This is done by automatically changing post-quantum keys on an ongoing basis.
Apple says PQ3 has been designed to combine post-quantum algorithms with classic Elliptic Curve cryptography, requiring an attacker to defeat both the classic and the post-quantum cryptography in order to gain access to communications. The company notes that PQ3 has been designed to amortize the message size to avoid excessive overhead.
While we may be many years away from practical quantum computing attacks, Apple says the introduction of PQ3 is useful now against so-called ‘Harvest Now, Decrypt Later’ attacks. This refers to threat actors collecting and storing encrypted communications now with the goal of decrypting them in the future when quantum computers become available.
Apple has published a detailed security analysis of the PQ3 protocol for interested security researchers and cryptographers.
The protocol underwent a mathematical analysis by Douglas Stebila of the University of Waterloo, who found that the protocol “provides confidentiality even in the presence of some key compromises”, and a team from ETH Zurich, which found that the protocol is efficient even “in the presence of very strong adversaries who can corrupt parties or possess quantum computers”.
PQ3 is currently in beta and it will be rolled out with the upcoming release of iOS 17.4, iPadOS 17.4, macOS 14.4, and watchOS 10.4. The new protocol will be enabled by default for communications between devices that support PQ3.
“As we gain operational experience with PQ3 at the massive global scale of iMessage, it will fully replace the existing protocol within all supported conversations this year,” Apple said.
Related: AI Helps Crack NIST-Recommended Post-Quantum Encryption Algorithm
Related: In Other News: WEF’s Unsurprising Cybersecurity Findings, KyberSlash Cryptography Flaw














