Amazon this week activated its proprietary mesh network known as Sidewalk, linking tens of millions of Amazon smart devices, each sharing a tiny sliver of their bandwidth to provide a wide network of connectivity even when and where WiFi service is poor or unavailable.
Like all new technologies, it is being promoted with attractive use cases – such as the ability to determine that a pet has gone walkabout and detect that pet’s current whereabouts. More compelling is the ability to track and find wandering dementia patients through their smart watch.
But also like all new technology it comes with concerns – in this case, personal privacy.
What is Sidewalk
Amazon describes it as “a shared network designed to help customer devices work better, both at home and beyond the front door. Operated by Amazon—with no charge to customers—Sidewalk helps simplify new device setup, extends the working range of low-bandwidth devices, and helps devices stay online, even if they are outside the range of the user’s home wifi.” It is only available in the U.S. for now.
Mesh networks like this are only viable if there are sufficient user devices, with enough of their owners trusting Amazon with the data passing over their network. This explains why the default setting contained in the Sidewalk software downloaded and installed by Amazon in participating devices is ‘on’ – making Sidewalk opt-out rather than opt-in. It also explains why the phrase “privacy and security is foundational” to the design of Sidewalk occurs five times in the Amazon Sidewalk Privacy and Security Whitepaper (PDF). (Note that the use of ‘is’ implies that Amazon considers privacy and security to be a single concept – which is itself a little worrying. Privacy and security are separate issues.)
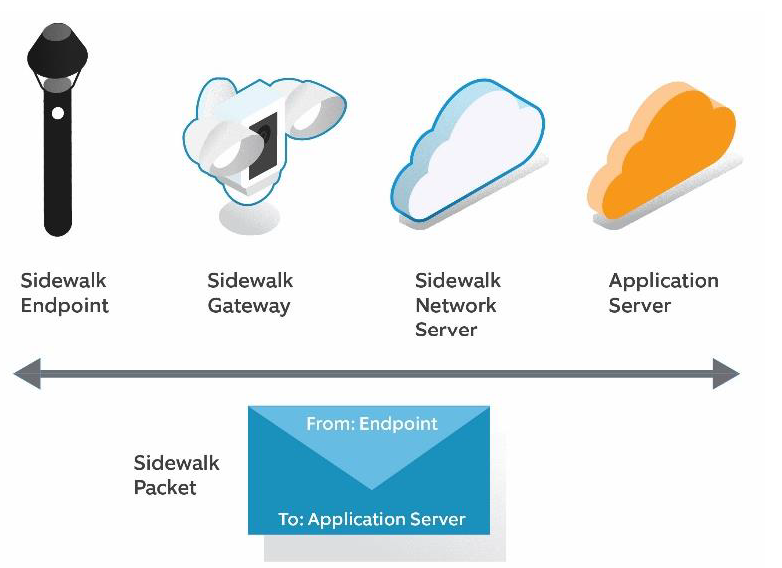
The paper outlines the architecture and security protections for Sidewalk. The primary components are endpoint, gateway, network server and application server. The gateways (an Amazon device like the Ring Floodlight Cam) pass packets using 900 MHz (LoRa and/or frequency-shift keying (FSK), and/or Bluetooth Low Energy (BLE) between the endpoint and the Sidewalk Network Server (SNS). The SNS is responsible for verifying incoming data, routing packets to the right destination, and keeping the network time-synchronized. This is operated by Amazon.
The endpoint is a low-power smart device “such as,” says Amazon, “leak sensors, door locks, lights, or devices you can attach to valuables or a pet to know where it is.” The endpoints are hosted by a separate application server, which implements the business and desired functionality. These are managed by the endpoint manufacturer, which could be either Amazon or a third party.
Understanding privacy and security
Privacy and security are obtained through data minimization, encryption, and rolling transmission IDs. Minimization limits the amount of visible data that passes through the network – so, for example, the SNS needs to have routing data, but does not know the contents of the packets or commands being sent over Sidewalk.
Packets crossing the network have three layers of encryption to ensure data is visible only to the intended party. Devices entitled to join the network can only do so with the use of unique Sidewalk credentials. These are used with similar credentials for the gateways and SNS servers used during device registration, authenticating the device and deriving unique session keys between device and server. Encryption keys are derived from the session keys using algorithmic encryption functions.
During data transmission, the SNS changes the TX-ID to a different unique identifier every 15 minutes. Backtracking to the source device is made difficult by the SNS by periodically flushing the previous IDs.
Amazon has attempted to design security into Sidewalk – and its efforts have been welcomed by some commentators. ZDNet reported, “Having read Amazon’s privacy and security whitepaper, and looking at Amazon’s track record over the years, I’d have no problems using Amazon Sidewalk. Amazon has put a great deal of effort and engineering into this, and it’s a clever solution to a problem that affects more and more people who have an ever-expanding ecosystem of IoT hardware in their homes.”
Experts are cautious
Other commentators are more cautious. One thing to note is that although currently aimed at the smart home market, Sidewalk will inevitably over time encroach into the office and even the factory floor. Think BYOSidewalk in the office, and industrial IoT in the factory.
“Despite Amazon’s assurance of security and privacy” warns Bob Rudis, chief data scientist at Rapid7, “organizations with any Sidewalk-enabled device should proactively opt-out of being part of the network. Individuals/households should consider doing the same until researchers and policymakers have had a chance to fully evaluate the offering – including any liability one might incur if it is, indeed, possible someone could perform legally questionable network actions via your home or work network connection.”
He adds, “As with all things digital in our modern era, you should also regularly check to make sure you haven’t accidentally opted back into Sidewalk via an innocuous Terms of Service acceptance, default setting on some checkbox when checking your cart out, or missing a voice memo due to an Alexa hiccup.”
Sidewalk may look secure on paper, but it hasn’t yet been tested by adversaries. “Even though the security architecture seems solid,” says Roy Horev, co-founder and CTO at Vulcan Cyber, “these things tend to surface vulnerabilities, and Amazon has been called out for such cases in the past. The fact that you literally share your home devices with your neighbors raises the risk level to a new level. The location of participating devices might be disclosed over the public network in the form of a ‘find-your-pet’ feature.”
This is admitted by Amazon in its whitepaper: “Just like your wifi router, it’s possible to look at signals to try to triangulate the location of a device on the Sidewalk network.” The encryption may prevent visibility into the content of the packets, but it won’t prevent location of the source.
History tells us that there will be bugs in Sidewalk – no product has ever launched completely bug-free – and bugs inevitably lead to vulnerabilities. “I await the news of the first researcher to successfully connect an unauthorized device,” comments Wendy Grossman, author of net.wars.
Even if Amazon rapidly fixes vulnerabilities, continues Horev, “do you trust your neighbor to patch their devices fast enough to avoid risk? You shouldn’t. They are a part of your network when using sidewalk. Do you trust 3rd party developers creating plugins to be secure enough? Again, you shouldn’t.”
The theory behind Sidewalk looks good and offers some compelling use cases. But potential users should remember that ultimately, Amazon is not doing this to benefit users, but to benefit Amazon. The best advice is to be cautious. Sidewalk’s first users will be guinea pigs; something that is by definition poor security. Opt out for now, monitor Sidewalk security over the next 18 months, and only then consider whether it is worth opting in.
It’s equally important for cybersecurity officers to consider that many users won’t be following this advice. Those with responsibility for workplace cybersecurity need to start preparing for their staff to bring Sidewalk into the workplace, whether intentionally or through carelessness. Sidewalk may create a new potential security risk, so damage limitation, threat mitigation and risk minimization need to be considered and planned for immediately.
Related: Amazon Alexa Vulnerabilities Could Have Exposed User Data
Related: Amazon Exposes Customer Names, Email Addresses
Related: Amazon Digital Assistant Alexa Gets New Skill: Amnesia
Related: Cybercriminals Target Amazon Third-Party Sellers With Password Reuse Attacks















