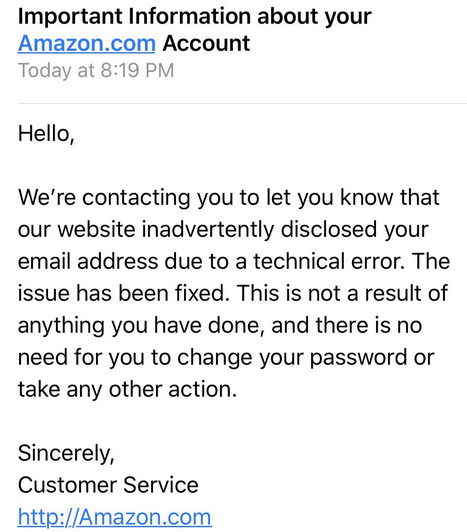
Amazon informed some customers this week that their name and email address were exposed due to a “technical error,” but the company provided very few other details.
The e-commerce giant claims the issue has been addressed and has told users that they do not need to change their password or take any other action. It has also revealed that the incident is not a result of something customers have done.
Many recipients initially believed the emails were part of a scam as the message did not address them by name and its signature included a link to “http://Amazon.com” – some found the lack of HTTPS and the capital “a” suspicious.
It’s unclear what caused the technical error and how many users are impacted. Twitter has been flooded by people saying they received the email, including individuals from the United States, the United Kingdom and Australia.
Unsurprisingly, many users are unhappy with the lack of transparency. Amazon has refused to share any additional details with customers or the press.
Some believe the incident may be related to the firing of an employee last month for sharing customer email addresses.
At the time, Amazon said an employee had been terminated for handing over customer email addresses to a third-party seller that had been blocked as a result of the incident. The Wall Street Journal previously reported that Amazon had been investigating employees sharing customer data with sellers in exchange for bribes.
“I wouldn’t hurry with premature conclusions until all technical details of the incident become clear,” Ilia Kolochenko, CEO and founder of web security company High-Tech Bridge, told SecurityWeek. “Based on the information currently available, it is technically incorrect to call this incident a ‘data breach’. This rather looks like an inadvertent programming error that made some details of Amazon’s profiles publicly available to random people.”
“Amazon’s reaction seems to be quite prompt, however an official statement would certainly be helpful to prevent any speculation and unnecessary exaggeration of the incident and its scope,” Kolochenko added.
Related: Cybercriminals Target Amazon Third-Party Sellers With Password Reuse Attacks
Related: Amazon Forces Password Resets after Possible Security Breach














