New Technology Enforces Mobile Security Policy on a “Situationally Aware” Basis
AirPatrol Corp. today unveiled ZoneDefense, a monitoring and security technology that lets enterprises detect any mobile device on premise, track its location, check its compliance with company policy and enforce rules based on where the user is located and who is nearby.
![]() Imagine a board meeting where sensitive conversations take place and confidential presentations are made. With the features in today’s smartphones, users are easily able to record audio, take photos, videos and of course, make calls at any time—posing a threat in situations where sensitive information is prevalent. That being said, forcing a board member to check his or her mobile device at the door may be a bit much to ask.
Imagine a board meeting where sensitive conversations take place and confidential presentations are made. With the features in today’s smartphones, users are easily able to record audio, take photos, videos and of course, make calls at any time—posing a threat in situations where sensitive information is prevalent. That being said, forcing a board member to check his or her mobile device at the door may be a bit much to ask.
Security Resource: Advanced Fraud Threats in Mobile Environments
AirPatrol’s ZonDefense can help defend against mobile threats beyond the typical access controls and data protections that many enterprise mobile management solutions provide. Utilizing commercial wireless bands and Wi-Fi, ZoneDefense’s technologies can track a device within a couple of meters of its exact location. In the case of a board meeting, ZoneDefense could, for example, automatically disable cameras and microphones as well as outgoing calls on smart phones detected in the boardroom.
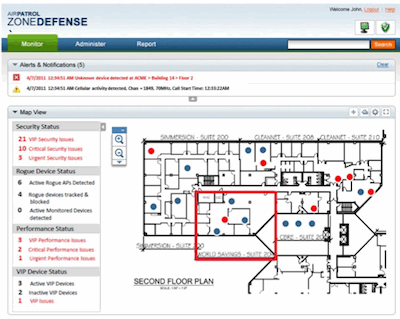
With ZoneDefense deployed, any mobile device that is detected — whether it is a managed device or an unknown device — can follow specifically-defined policies based on where it is located and who is nearby. In another example use case, a mobile device may be permitted to do file sharing in an approved area of the headquarters building might have file sharing turned off in another part of the facility. Enterprises also can set up the system to trigger an alert when an unknown device enters a secure zone such as a boardroom or trading floor.
“ZoneDefense revolutionizes the way we monitor and manage the very fluid and ubiquitous mobile device layer through intelligence,” stated Tom Kellermann, CTO of AirPatrol. “Through continuous wireless monitoring and situational awareness, AirPatrol’s ZoneDefense has an advance persistent response that is paramount in today’s wireless security.”
ZoneDefense currently supports iOS (iPhones and iPads) and BlackBerry platforms, but will support Android later this year.
Related Reading: Advanced Fraud Threats in Mobile Environments














