A researcher found a way to deliver malware to macOS systems using a Microsoft Office document containing macro code. The victim simply has to open the document and no alerts are displayed.
Macros enable Office users to automate frequent tasks using VBA code. A macro added to an Office document can be triggered when the file is opened, a feature that cybercriminals started exploiting many years ago to execute malicious code that is typically designed to deploy a piece of malware.
This is why Microsoft has disabled the execution of macros by default — users have to explicitly enable macros if they want to execute the code in a document. However, that has not discouraged threat actors, who often rely on social engineering to trick victims into enabling macros. In response, Microsoft has introduced a feature which ensures that the macro code is executed in a sandbox even if the user allows it to run.
While a vast majority of macro-based attacks target Windows systems, in recent years, researchers spotted some attacks aimed at macOS users, including one campaign that has been linked to North Korea’s Lazarus group.
However, Patrick Wardle, principal security researcher at Apple device management company Jamf, pointed out that these attacks were not very sophisticated and they likely had a low success rate, as the targeted user would explicitly have to enable macros, none of the attacks was able to escape the application sandbox even if the macro was executed, and Apple’s quarantine feature and notarization checks could have blocked additional payloads.
Wardle revealed this week that he identified a way to make macro-based attacks against macOS systems much more efficient. He has described an exploit chain that bypassed all of the aforementioned security mechanisms, allowing an attacker to deliver their payload without any warning — the victim simply had to open the malicious document.
First, in order to have the macro code automatically executed when the victim opened the document, without having to explicitly enable macros, the researcher used a method that was disclosed in 2018. Pieter Ceelen and Stan Hegt showed at the time that XML macros in SYLK files were automatically executed in Office 2011 for Mac. XML is the macro programming language used before VBA and SYLK is an old Microsoft file format designed for exchanging data between applications.
Last year, an advisory published by CERT/CC revealed that the vulnerability still worked on more recent versions of Office for Mac if the user had enabled the “Disable all macros without notification” option.
“As this is the most ‘secure’ setting it may often be set, especially by security conscious users or organizations,” Wardle explained in a blog post.
Using this method would ensure that the attacker’s macro is executed without any alerts being displayed on the targeted device. However, the code would still run in a sandbox.
A sandbox escape that would be useful in this attack was disclosed in 2018 by researcher Adam Chester. His method was patched at the time by Microsoft, but Wardle recently found a way to bypass the fix, which would ensure that the malicious code is run outside the sandbox on the next login.
All that is left now is to bypass Apple’s notarization checks, which prevent code downloaded from the internet from executing. Notarizing a piece of software is an automated process in which Apple’s notary service scans the software for malicious code. Wardle overcame this hurdle by abusing the Archive Utility app in macOS.
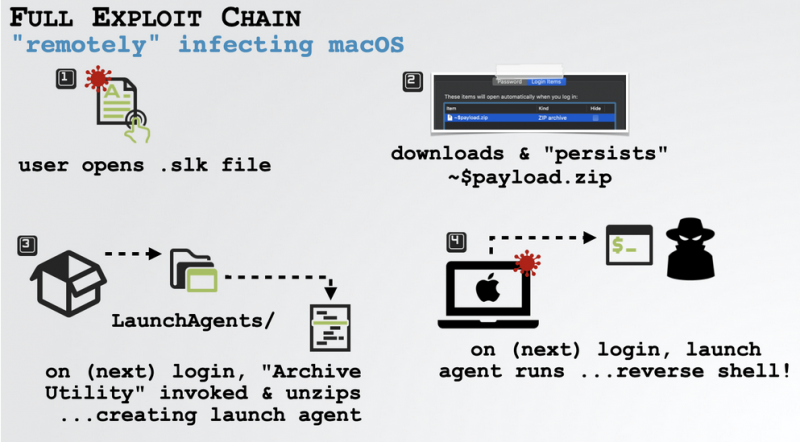
He demonstrated the exploit chain by spawning a reverse shell, which he used to deliver the OSX.WindTail backdoor.
The researcher notified Apple about his findings and the company silently patched the vulnerabilities with the release of macOS 10.15.3. The company later edited its advisory to credit Wardle, but it did not assign a CVE identifier.
Wardle is an expert in Mac security and his research projects over the past years have led to the discovery of some interesting vulnerabilities. This week he announced a new book series, The Art of Mac Malware, which can be read for free online.
Related: Repurposing Mac Malware Not Difficult, Researcher Shows
Related: Hackers Can Bypass macOS Security Features With Synthetic Clicks














