Repurposing Mac malware is not a difficult task for someone with reverse-engineering skills, and it’s a far simpler approach compared to writing malware from scratch, a researcher has demonstrated.
The research was conducted by Patrick Wardle, Mac security expert and principal researcher at Apple device management platform provider Jamf. Jamf acquired Digita Security, a macOS security company co-founded by Wardle, last month.
Threat actors have been known to repurpose existing malware — the NSA’s Tailored Access Operations (TAO) unit has reportedly done it, and Chinese cyberspies are said to have repurposed leaked NSA hacking tools. Repurposing malware can have several advantages and in the case of nation-state actors it makes attribution more difficult.
Wardle told SecurityWeek that one of the goals of his research is to show that its rather trivial and far less time-consuming to repurpose malware than to develop a completely new piece of malware.
“Being able to take a complex, well-written piece of malware (that a competent software engineer has created) and repurpose it, is a far simpler approach than trying to write one from scratch,” Wardle said.
“Also given the benefits of (mis)attribution and disposability of these tools (if they get caught, no problem, just repurpose another one), using repurposed malware is very compelling,” he explained.
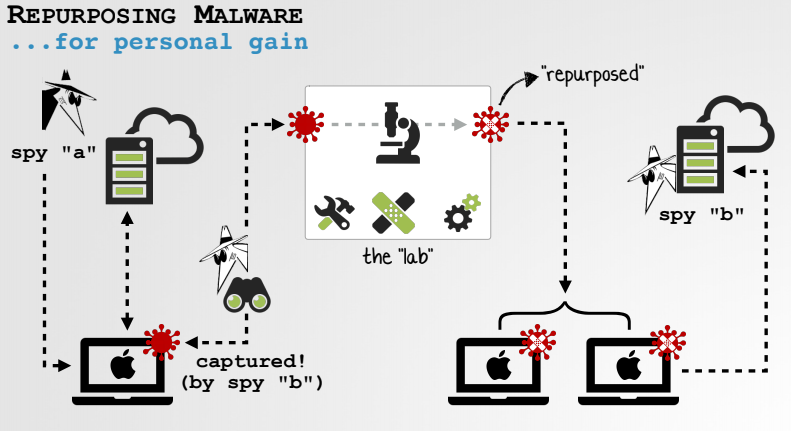
He demonstrated this theory by repurposing several known pieces of Mac malware, including the FruitFly backdoor, the CreativeUpdate cryptocurrency miner, the KeRanger ransomware, and the Windtail backdoor.
Assuming that no source code is available, the challenges of repurposing a piece of malware include identifying all the relevant logic, understanding the command and control (C&C) protocol, modifying (patching) the original malware, and creating a C&C server that can communicate with it.
Specifically, these activities can include creating a custom installer, changing the address of the C&C server in the malware, and changing the wallet address (in the case of cryptocurrency miners).
There are plenty of malware samples to choose from. Objective-See, a website run by Wardle, hosts over 120 Mac malware samples that are freely available for download.
Wardle has also demonstrated several techniques for making minor modifications to known Mac malware so that they are no longer detected by signature-based security solutions, such as Apple’s XProtect and Malware Removal Tool (MRT).
The bypass methods analyzed and successfully executed by Wardle include changing a single byte in the malicious file, unsigning and resigning components to bypass certificate revocation mechanisms, and simply renaming components. While the expert has tested these methods against Apple tools, he is confident that third-party antiviruses are just as easy to bypass, including through the use of free obfuscation services.
The solution to detecting these types of threats, Wardle says, is focusing on potentially malicious behavior rather than signatures. This includes file activity monitoring for actions associated with methods of malware persistence, detecting access to the device’s microphone and camera, monitoring for keyboard “event taps” that could indicate the presence of a keylogger, and detecting synthetic clicks.
The researcher has developed several free tools that can help detect many of these actions. Digita Security created a commercial endpoint protection product for enterprise Mac fleets, GamePlan, that can also detect synthetic clicks.
Wardle is presenting his research on Friday at the DEFCON hacking conference in Las Vegas.
Related: Mac Malware Delivered via Firefox Exploits Analyzed
















