Researchers at web application security firm RIPS Technologies have analyzed 44,705 of the roughly 48,000 plugins available in the official WordPress plugins directory and discovered that more than 8,800 of them are affected by at least one vulnerability.
The company downloaded all the plugins and used its static code analyzer to check the ones that have at least one PHP file. An analysis of the size of these plugins showed that roughly 14,000 of them have only 2-5 files and only 10,500 of them have more than 500 lines of code.
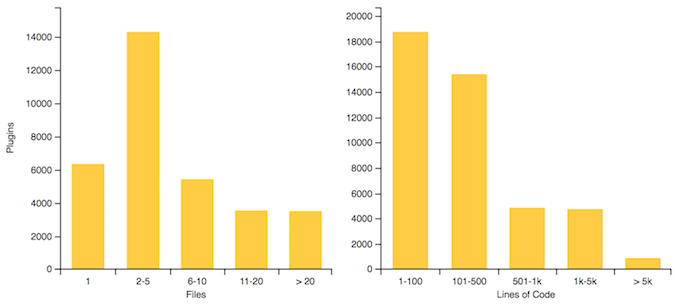
Researchers determined that of the plugins with more than 500 lines of code, which have been classified as “larger plugins,” 4,559, or 43 percent of the total, contain at least one medium severity issue (e.g. cross-site scripting).
RIPS’s analysis showed that nearly 36,000 of the plugins did not have any vulnerabilities and 1,426 had only low severity flaws. Medium severity bugs have been identified in more than 4,600 plugins, while high and critical security holes have been found in 2,799 and 41 plugins, respectively.
A total of 67,486 vulnerabilities have been discovered in the plugins, which indicates that the applications that do have flaws have a lot of them. Experts noted that a majority of plugins don’t have weaknesses due to their small size (i.e. have fewer lines of code).
As for the types of vulnerabilities affecting these plugins, unsurprisingly, more than 68% are cross-site scripting (XSS) issues and just over 20% are SQL injections. XSS flaws can pose a serious risk in the case of WordPress websites, but exploiting them requires administrator interaction. SQL injections, on the other hand, can be exploited without user interaction and attacks can be automated.
Between January and December 2016, a honeypot operated by RIPS captured more than 200 attacks targeting WordPress plugins, including 69 against Revolution Slider, 46 against Beauty & Clean Theme, 41 against MiwoFTP and 33 against Simple Backup. These attacks involved easy-to-exploit vulnerabilities that were known and well documented.
RIPS pointed out that they may not have found all the vulnerabilities affecting the plugins they analyzed, and it’s uncertain if the flaws they identified are exploitable.
Related: Hackers Can Exploit Roundcube Flaw by Sending an Email
Related: Hacked WordPress Sites Target Random Users
Related: Backdoor Uploaded to WordPress Sites via eCommerce Plugin Zero-Day
Related: WordPress Flaw Allows XSS Attack via Image Filenames













