There is a saying in the InfoSec world – you can’t patch human stupidity. It isn’t hard to prove that statement depending on the situation, but a new account on Twitter is making the task a simple one. The account, @NeedADebitCard, is re-tweeting people who are openly declaring their intent to share the wealth (what little of it there is) by posting pictures of their debit and credit cards for all to see.
Complete with names, card numbers, expiration dates, and in some cases CVV code (the security code that appears on a statement or activation letter), the Darwin Award hopefuls seem all to willing to share their respective credit lines.
(Image Blurred by SecurityWeek for Privacy and Security Reasons)
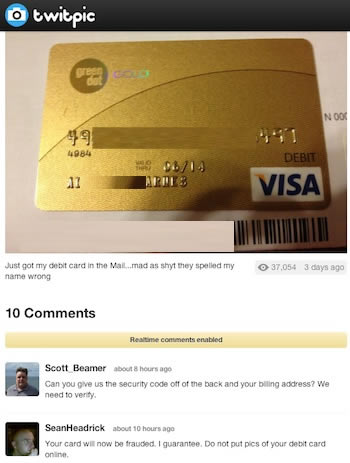
It would be tragic if these images were stolen, or perhaps unknowingly leaked. However, they were intended for the public to see, and perhaps use, because the card owners willingly published the images themselves. Always willing to offer assistance and lulz, some supporters of Anonymous were only too happy to re-tweet some of the more revealing images, as were a few others who are not known for their hospitality.
Most of the images were taken with an awful image service called Instagram, while others were simply uploaded with TwitPic or something similar. Instagram, at the time this rant was written, is at least attempting to help the foolish by deleting the images that contained sensitive information. As for those on other image services, they’re on their own it seems.
There has been talk of legality; questions focused on if the re-tweeting done by NeedADebitCard is in fact a crime. After speaking to those familiar with such issues, it seems that anyone wanting to sue for the re-tweeting has an uphill battle. As they are the reason the card image existed in the first place.
Whoever runs the NeedADebitCard account appears to have done so in order to promote awareness, as the biography section simply states, “Please quit posting pictures of your debit cards, people.”
Most reading this won’t need the advice offered by @NeedADebitCard. In fact, of the images posted and since removed (though they are cached online), most of them were teens.
Thus, while most of the techies reading this know better, it might be wise to explain (rehash) the foolishness of such an act to the kids and significant others who stopped thinking for a brief moment during their financial joy.
The L.A. Times had some interesting stats in their coverage of the dunderheads on Twitter, which puts things into perspective.
“According to the U.S. Bureau of Justice, 8.6 million American households experienced identity theft in 2010, with unauthorized credit card use accounting for much of the increase from the 6.4 million households victimized in 2005. Families lost a total of $13.3 billion, with an average of $2,200 lost per household affected. A 2011 report from Javelin Strategy & Research cited by the Wall Street Journal said social media and smartphone use accounted for recent increases in identity theft.”
In closing, there’s nothing to say. All the advice in the world comes down to a harsh reality. No matter how hard security professionals try, no matter how loud they shout, you can’t patch human stupidity.












