San Jose, California-based Zscaler, a provider of cloud-based security solutions, today added new analytics technology to its cloud security suite designed to provide enterprise security teams with real-time visibility into employee Internet activity across web, cloud email, and mobile application platforms.
The new data visualization capability utilizes real-time data gained from the processing of more than 10 billion Internet transactions across Zscaler’s network, something the company is pushing under the term “Big Analytics”.
 With the visualization tool, enterprise security teams are armed with instant, actionable insight into security threats, user productivity, and compliance violations, no matter where end users may be located or what device they may be using.
With the visualization tool, enterprise security teams are armed with instant, actionable insight into security threats, user productivity, and compliance violations, no matter where end users may be located or what device they may be using.
In addition to providing visibility into Internet traffic across web, email, and mobile platforms, Zscaler says customers can also benefit from:
• Role-based access control to ensure appropriate policy and data reporting capabilities match the appropriate security level for the administrator.
• Advanced report creation capability leveraging an API layer. Customers and partners can effortlessly back up and duplicate reports;
• Log storage simplification with automatic storage of logs using Nanolog, a Zscaler technology for massive compression of log data for scalable storage along with very fast retrieval methods. According to the company, with Nanolog, there’s also no need for data correlation nor data aggregation from multiple recorders;
• Cross platform, device, and location visibility. Users can now switch devices, locations, or move from web/email/mobile communication platforms, but still be correlated in the Zscaler Security Cloud.
Screenshot of the Zscaler Security Dashboard
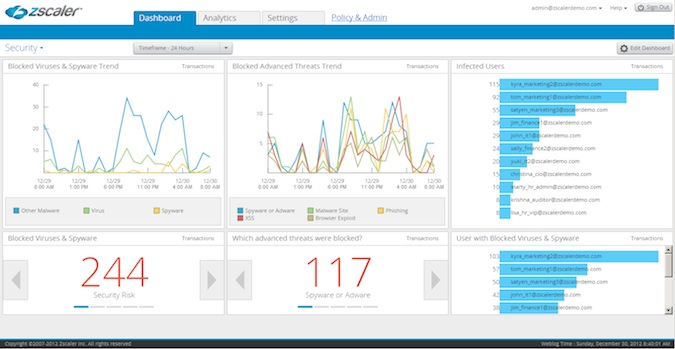
“The new analytics capability in the Zscaler Security Cloud delivers a number of benefits that really raise the bar for security analytics performance, scope and cost-savings,” Dr. Manoj Apte, senior vice president of product management at Zscaler.
“For example, Zscaler eliminates reporting across multiple locations, which typically requires coordination of multiple administrators, deployment of additional services to collect log data, and personnel to run scripts and ensure log collection and data visualization are properly done,” Apte explained. “We also eliminate personnel costs related to reporting and forensic investigation, compliance responses (internal and external), and additional hardware and storage for log analysis.”













