Zoom Security Risks, Privacy and GDPR Compliance
Home working and learning has led to a boom in videoconferencing, with Zoom a major beneficiary. But concerns over privacy and security raise important questions: is Zoom safe, and is it even GDPR compliant?
Security concerns revolve around the recent discovery of several vulnerabilities taken with the length of time it has taken Zoom to fix earlier vulnerabilities. Privacy concerns focus on a lack of transparency around the user or meeting data retained by Zoom, and who else has access to it. We will concentrate on the privacy issues in this article.
Data retention and third-party access concerns are typified by the recent discovery that the Zoom iOS app had been passing data to Facebook even where the iOS user had no Facebook account. There was no indication in Zoom’s privacy policy that this was happening (Zoom has stopped this, but iOS users will need to download the latest app version to prevent it continuing).
There are two concerns here: the lack of transparency and the distribution of information to a third party without user consent. “This is a clear breach of GDPR,” Tara Taubman-Bassirian, a French-born, London-Based lawyer and privacy advocate, told SecurityWeek. “With the lack of transparency, the host holds many capabilities that are unknown to the participant, such as recording and further broadcasting.”
The consent issue is a complex one, which will require careful consideration by Zoom if it is to be solved. GDPR holds that consent for collecting personal data must be freely given, and that if there is an imbalance of power between the parties, it cannot be a free choice and that any consent obtained is invalid. There is already a precedent for this. In September 2019, a school in Sweden was fined $20,000 for using facial biometrics to track 22 students. The parents had given their consent, but the data protection regulator ruled, “consent was not a valid legal basis given the clear imbalance between the data subject [the students] and the controller [the school].”
There is the potential for this same argument to be used in the current work from home environment, for both office workers and schoolchildren. Any invitation to a teleconference is effectively an instruction with an imbalance of power and little realistic option to decline. It is possible that many COVID-19 instigated teleconferences are being held in contravention of GDPR’s consent rules. Zoom describes itself as the data processor rather than the data controller (which is the host). If this argument is supported by the GDPR data regulators, and the meeting hosts keep a recording of the meeting on their own servers, it means that the host is responsible for the data under GDPR.
This is an important aspect that might not be recognized by the hosts. Valid consent becomes even more important, and it should, suggests Taubman-Bassirian, “be of the higher standard as data collected and recorded are biometrics capable of identifying individuals” — and in some cases will include children.
Zoom appears to be making efforts to solve the issues that have been raised over the last few weeks. In a blog published Wednesday, it says, “We are looking into each and every one of them and addressing them as expeditiously as we can. We are committed to learning from them and doing better in the future.” One immediately welcome statement is “we do not sell our users’ data, we have never sold user data in the past, and have no intention of selling users’ data going forward.”
The blog explains the pressure the company is under. Where last year the maximum number of daily meeting participants was around 10 million, it is now more than 200 million, which now includes 90,000 schools across 20 countries. But the issues pre-exist the current surge in use — they have not been created by the expansion.
Zoom further explains that the platform was designed for business users, and the influx of home workers and schoolchildren has been a surprise. But the need for privacy and security does not differentiate between corporations, individual workers at home, and schoolchildren — so, neither of these arguments have any bearing on the current issues. Indeed, they rather raise another question since they indicate a lack of privacy by design or default — which is a requirement under GDPR.
One of the improvements Zoom is working on is to improve its transparency and clarity. It has admitted, in a separate blog, that that what it marketed as end-to-end encryption of its services is no such thing.
Jarosław Kamiński, principal consultant at F-Secure, explains the relevance. The encryption used means that communication between the Zoom server and the participant is encrypted and not susceptible to a man-in-the-middle attack. “E2E,” he continued, “means the communication is encrypted for the whole time and is inaccessible to the vendor. Without end-to-end encryption, a vendor has the technical capability to intercept / record the communication.” That doesn’t mean the vendor does this; but Zoom doesn’t specify that it doesn’t.
Zoom is also introducing a new transparency report. This is very welcome. The firm says it is, “Preparing a transparency report that details information related to requests for data, records, or content.” Notice the word ‘content’. An updated privacy policy issued on March 27 makes it clear that the Zoom cloud will contain recordings of all meetings that the host wishes to be recorded — so Zoom will always have access to some meetings’ content. What it doesn’t say is that it does not store any other meetings’ content. We know that since it does not use end-to-end encryption, it can intercept and store everything. We don’t know whether it does, nor how long it retains the content it says it stores.
This raises another question, since Zoom says clearly that it obeys national laws for government access to content. But Zoom is global in operation, which means that via the CLOUD Act, the U.S. government will have access to foreign data. This is worth considering, since apart from possibly sensitive commercial information, that content might even include confidential foreign government data.
On March 27, UK Prime Minister Boris Johnson tweeted that he had just, hours earlier, “chaired the first ever digital Cabinet”. The screenshot he shared makes it clear it was held on Zoom, and even shows the Zoom meeting ID number. Disclosing the ID number is not as concerning here as it might immediately appear because the meeting had finished and there was no chance for ‘zoombombing’ by third parties.
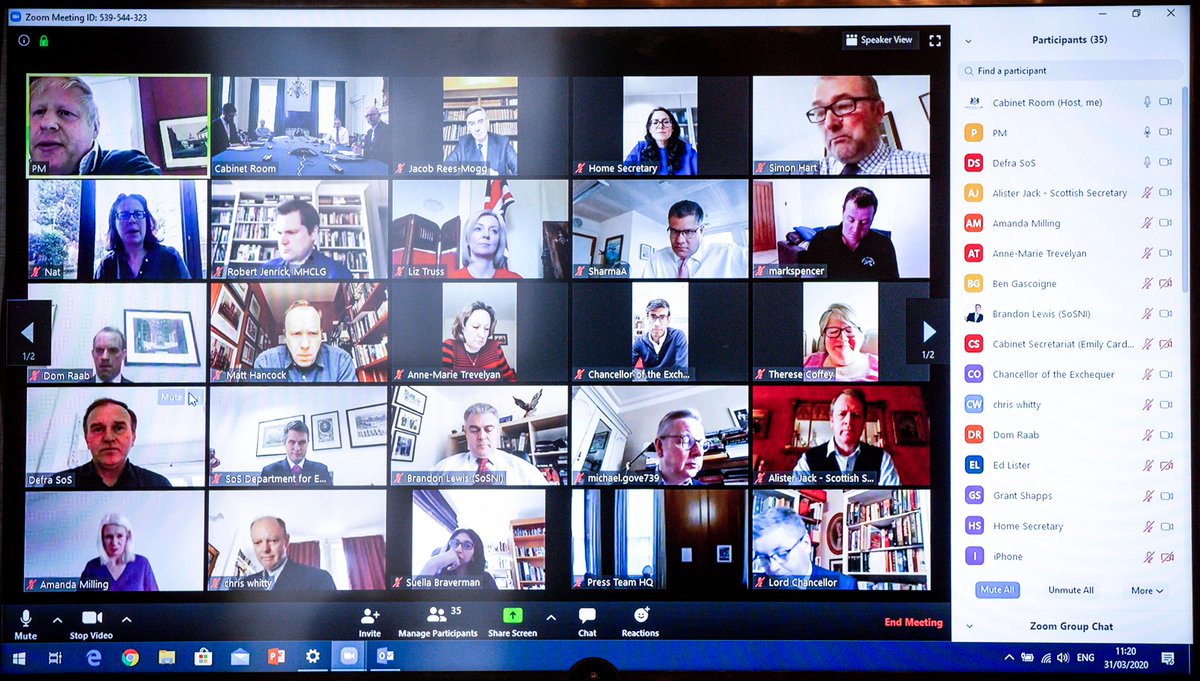
F-Secure senior researcher Andy Patel explained ‘zoombombing’. “A Zoom meeting ID is a relatively short numerical string that can likely be guessed or brute forced. By constructing an URL to potential meetings (by synthesizing the URL — usually just the Zoom URL, possibly expanded with the customer name, with the ID appended), someone can find and join meetings that aren’t password protected, even if they weren’t invited,” he told SecurityWeek. “As an extra bonus, some people have been posting screenshots from their Zoom meetings that include the ID, so when people find those, they all pile into the open meeting.”
However, in our current example, we do not know whether the host (either Boris Johnson or the Cabinet Office) asked for a copy to be kept by Zoom for future reference, or whether Zoom kept a copy by default. In either case, US intelligence agencies now could demand access to everything said within the meeting.
It would be natural to expect that the UK’s cyber guardians — in particular, the Cabinet Office and the NCSC — would have ensured Zoom’s privacy and security before allowing the prime minister to go digital. SecurityWeek asked both offices for clarification, but got none. The Cabinet Office did not answer our questions, but provided two unrelated comments, “National Cyber Security Centre guidance shows there is no security reason for Zoom not to be used for meetings of this kind.” It also said, “The MoD [referring to false reports that the MoD had banned the use of Zoom] uses Zoom to conduct cross-government meetings for official level business. There are no plans to review this.”
The implication is that the NCSC has examined Zoom and found it adequate. This doesn’t seem likely, since the only comment provided by the NCSC, so far, firmly passes the buck back to the Cabinet Office: “Cabinet Office are leading the response on Zoom, so for a statement I’d recommend getting in touch with press office via [their email address].”
Whether the NCSC has conducted its own tests on Zoom or not, there nevertheless seems sufficient privacy issues (past and present) to wonder if Zoom is adequately GDPR (or the UK’s Data Protection Act implementation of GDPR) compliant. Here SecurityWeek asked the Information Commissioner’s Office for a comment.
The reply was this: “”The coronavirus pandemic has led to a rise in use of video conferencing tools as a valuable way for people to communicate. Any such technology must be transparent with users about how their data will be processed, as well as giving users choice and control. At this stage we are considering various concerns that have been raised regarding video conferencing apps.”
There is no specific reference to Zoom, but we can assume that it is high on the list of videoconferencing tools being considered. Other European data processing regulators are likely to be doing similar. On the surface it would appear that Zoom has a case to answer — but Zoom hosts must also consider their own exposure as data controllers — especially regarding the valid consent issue.
Whether Zoom should be investigated — or even fined if found to be in violation — is a different question. “It is my opinion,” Brittany Roush, Director at the Crypsis Group, told SecurityWeek, “that having that kind of flexibility to ensure that critical services can carry on, especially in a crisis, does not take the teeth from the CCPA and GDPR. If anything, it demonstrates that the regulatory bodies are carrying out their essential function — which is to ensure that companies protect consumer data… In many ways, the CCPA and GDPR should take a page from HIPAA, which lowered security standards for telehealth in order to manage the critical healthcare demands of the pandemic… we do not have the luxury of time on our side to devise perfect solutions.”
Related: Trojanized Zoom Apps Target Remote Workers
Related: Vulnerability Allowed Attackers to Join Zoom Meetings
Related: Zoom Conferencing App Exposes Enterprises to Attacks
Related: WebEx, Zoom Meetings Exposed to Snooping via Enumeration Attacks










