Zeus Trojan – Targeting Verified by Visa and MasterCard SecureCode Security Programs during Online Banking Sessions
Secure browsing services provider Trusteer, warned today that the Zeus (Zbot) continues to attack and is targeting online banking customers of 15 leading US financial institutions by exploiting two trusted credit card security programs.
When an online banking customer has initiated a secure online banking session, the Zeus Trojan injects a fake version of the familiar Verified by Visa and MasterCard SecureCode enrollment screen. It then prompts users to enter their social security number, credit or debit card number, expiration date, and PIN or CSV code.
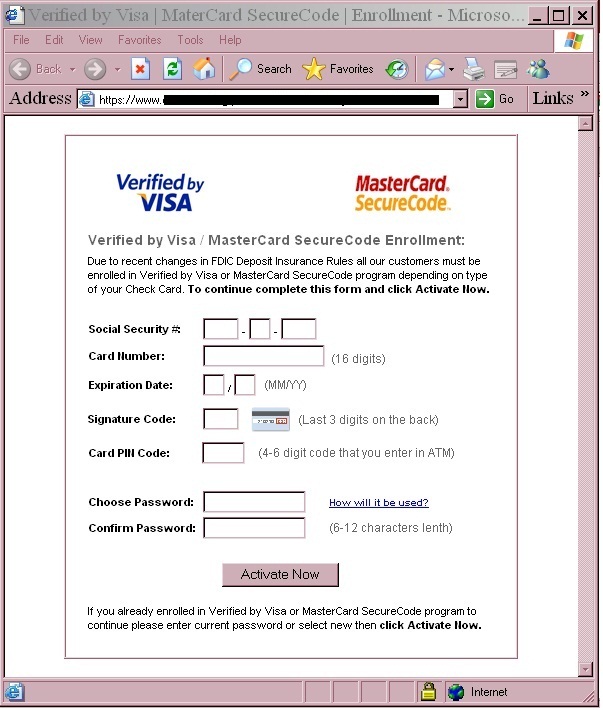
The information gathered by Zeus is used by fraudsters to commit ‘card not present’ transactions with retailers that employ Verified by Visa and SecureCode protection. This stolen data allows criminals to impersonate their victims and register with these programs to ensure fraudulent transactions pass through fraud detection systems undetected.
“Advanced, stealthy Trojans like Zeus that are detected less than 46% of the time are readily available to online criminals who are interested in stealing information for illegal gain,” according to Uri Rivner, Head of New CyberCrime Technology at RSA, The Security Division of EMC.
Trusteer discovered this new in-session phishing attack, and was able to collect Zeus configurations and code samples from infected computers. This version of Zeus attempts to trick online banking customers into surrendering their personal and credit/debit card data by claiming new FDIC rules require that they enroll in the Verified by Visa / MasterCard SecureCode program to protect their accounts.
“While some users may become suspicious when prompted to enter their credit/debit card information as part of the online banking login process, this attack uses the familiar Visa and MasterCard online fraud prevention programs to make the request appear legitimate,” said Amit Klein, CTO of Trusteer and head of the company’s research organization. “Fortunately, online banking customers protected by Trusteer Rapport are not vulnerable to this attack since it blocks HTML injection and prevents Zeus from presenting the fraudulent enrollment request.”
Zeus, also known as Zbot, WSNPOEM, NTOS and PRG, is the most prevalent banking malware platform for online fraud, and has been licensed by numerous criminal organizations. Zeus infects PCs, usually without users knowing or causing any other “noticeable” harm. The program then waits for the user to log onto a list of targeted banks and financial institutions, and then steals login credentials and other data which are immediately sent to a remote server hosted by cybercriminals. It can also modify, in a user’s browser, the genuine web pages from a bank’s web servers to ask for personal information such as payment card number and PIN, one time passwords, etc.
Anti malware detection of Zeus has a poor track record. In a 2009 report based on information gathered from 3 million desktops in North America and the UK Trusteer found that the majority of Zeus infections occur on antivirus protected machines. Specifically, Trusteer found that among Zeus infected machines 55% had up-to-date Antivirus protection installed. The population of machines infected with Zeus is enormous — one in every 100 computers according to Trusteer research.
Resource: The ZeuS Tracker tracks ZeuS Command&Control servers (hosts) around the world and provides you a domain- and a IP-blocklist















