White hat hackers have earned $545,000 for successfully demonstrating zero-day exploits targeting products from VMware, Microsoft, Google, Apple, D-Link, and Adobe at the 2019 Tianfu Cup hacking competition that took place over the weekend in Chengdu, the capital of China’s Sichuan province.
The highest single reward, $200,000, was received by the team named 360Vulcan for a VMware exploit that allows an attacker to escape from the guest virtual machine to the host.
VMware representatives were present at the event and confirmed that the exploit was successful against its VMware vSphere ESXi product. The company says it’s investigating the security flaws that made the attack possible and is working on addressing them. After last year’s Tianfu Cup, it took VMware only a few days to patch a $100,000-worth vulnerability disclosed at the contest.
The 360Vulcan team also demonstrated attacks against Microsoft Office, Microsoft Edge, Adobe Reader, and qemu-kvm on Ubuntu. The qemu-kvm vulnerabilities earned them $80,000, Edge vulnerabilities earned them $55,000, and for the Office exploit they received $40,000.
The 360Vulcan team was declared the winner of the Tianfu Cup, earning a total of $382,500 for their exploits.
Other participants demonstrated that they can hack Chrome, Safari, D-Link routers, and Adobe Reader.
The second-place team, ddd Team, earned a total of $83,750 for exploits targeting Edge, Chrome, Adobe Reader, and D-Link routers.
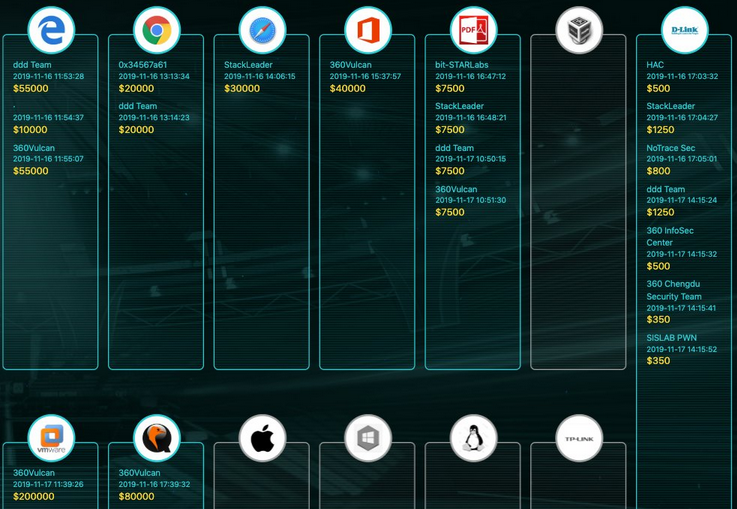
There were nearly 30 cases where the exploits either failed or participants simply gave up on their attempt. These targeted Edge, Chrome, Safari, Adobe Reader, Oracle VirtualBox, TP-Link and D-Link routers, Windows Server 2019, VMware Workstation, and the iPhone 11 Pro.
According to organizers, 11 teams demonstrated 20 successful exploit chains against eight products, which earned them a total of $545,000. It’s worth noting that last year’s event resulted in payouts totaling over $1 million.
Related: VMware Patches Flaws Disclosed at Pwn2Own 2019
Related: Bug Hunters Hack Samsung Galaxy S10, Xiaomi Mi9 at Pwn2Own
Related: Bug Hunters Earn $195,000 for Hacking TVs, Routers, Phones at Pwn2Own












