The Zero Day Dilemma
The statement that corporate cyber security is broken has become a cliché, but it’s all too true. If consumers do not trust global brands to keep their data secure, something’s clearly not working. In fact, the digital world has become a very dangerous place. There are literally millions of viruses floating around out there, but the ones that pose the greatest threat are the zero-day attacks, which involve malware that has never been seen before. According to a 2020 report (PDF) from Ponemon Institute, 80 percent of successful breaches are zero day attacks.
The number of these attacks has been steadily growing, from 17 in 2017 to 80 in 2021. Google alone has suffered at least six zero day attacks already this year. And while this trend is alarming, what’s even more disturbing is the highly organized development process behind these attacks that has evolved over time.
It frequently begins with freelance “bug bounty hunters,” who comb through the code of new software releases by major players looking for vulnerabilities. It’s a little like panning for gold. Vulnerabilities are hard to find, but if you have the right combination of skill and luck, you can definitely strike it rich. One malware vendor — yes, there are “vendors” in this ecosystem — has offered $2.5 million for Android vulnerabilities, and will pay comparable sums for other operating systems and enterprise scale applications. When these organizations get their hands on a vulnerability, they’ll be able to sell it for a lot more. Vulnerabilities that lend themselves to ransomware are especially valuable because most companies that become victims have no choice but to pay.
Why are zero day exploits so effective, and so highly prized by bad actors? The reason has to do with the way cyber security defenses work. Below is a diagram of the kill chain, initially adapted from military strategy by Lockheed Martin for the world of cyber crime.
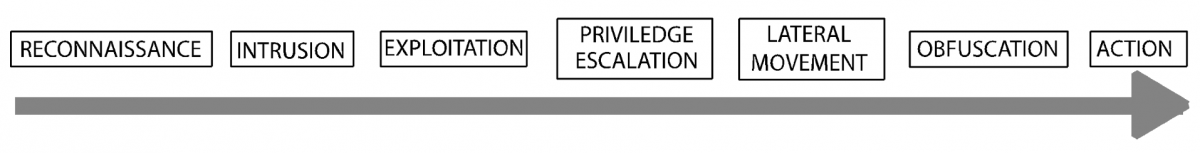
In the progression conveyed by this 7-step diagram, the cyber security industry has offered two types of responses. To the left side of the diagram there are preventive responses – attempts to block an intrusion in the first place. One such tactic is to train employees. Don’t click on that suspicious link! The weakness here is that even the most security -conscious employees are human and bound to occasionally make a mistake.
Another common preventive tactic is to deploy anti-virus software, often marketed in conjunction with email spam blocking. The premise behind this approach is that malware attached to phishing emails can be identified. The problem here is that these solutions ultimately depend on blacklists or patterns based on known attacks in the past. Even with AI, when something entirely new arrives, they have no basis for identifying it.
Moving further to the right, there are numerous solutions based on detecting anomalous behavior, either in respect to the network (including endpoints), applications or users (either human or computers). It’s important to remember that these systems do not prevent damage. They limit damage.
It’s somewhat ironic that almost every list of cybersecurity best practices includes one at the very far right: disciplined back-up processes. Reliable backup is a legitimate defense against ransomware, but it’s expensive, time-consuming and provides zero ROI. Also, to be frank, backup is almost always at the bottom of the IT to-do list, it isn’t always tested, and it doesn’t always work.
To sum up, the problem of the zero day attack has not been solved because every approach depends on knowledge of events that have happened in the past, whether it’s known malware or known “normal” network/application behavior that serves as a benchmark for spotting malware-caused anomalies.
The ideal zero day solution would not depend on known bad urls or patterns from the past. It would be able to intercept and evaluate URL clicks at every endpoint, isolate suspicious payloads, and actually see how they behave in isolation before passing them through. Such a solution would operate at the far left of the kill chain like spam/virus blockers, but it would not fail in the face of a zero day attack.
It has long been the conventional wisdom that preventive solutions like this are impossible to build. Now, however, given the power of the cloud, this approach is viable. Vastly superior preventive technology won’t let companies abandon their other security solutions any time soon, but for once it will put the security community ahead of the bad actors instead of having to play catch-up.














