Think of the major cyber-attacks from the past few years – the Sony hack, Target breach, Neiman Marcus, Snapchat Breach, Home Depot breach, or PayPal Hack. If you examine the common denominator between these attacks (and many other, less-known security breaches), you’ll notice two things. The first is well known – attacks have become sustained and highly targeted. Secondly, attacks thrive on security silos.
Advanced Attack Campaigns
First, let me quickly characterize the term ‘Advanced attack campaign’. These type of attacks will always involve an entity with a focused target and high motivation. Attackers are well-organized, have high security expertise, and are patient and persistent in identifying and implementing the optimal attack strategy by collaborating with multiple players.
Advanced attack campaigns are typically multi-vector, prolonged and adaptive to the defenses they encounter – unlike the defending side, which is inherently more rigid and structured around products and security solution silos.
Security Silos – a Sweet Spot for Attackers
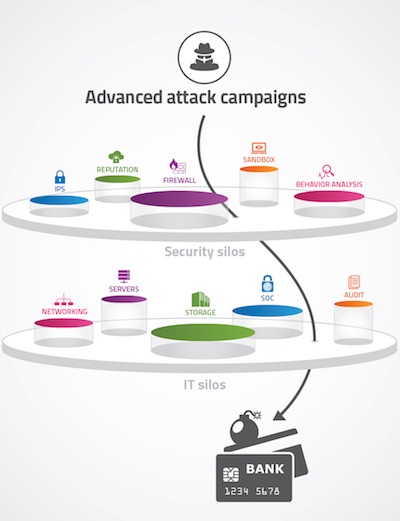 A typical large enterprise may have anywhere between 50-60 different security products and solutions deployed. Covering the entire security spectrum – intrusion prevention, anti-malware, network and user behavior analysis, WAF, and more – these products generate hundreds or thousands of alerts on a daily basis, creating quite a few challenges.
A typical large enterprise may have anywhere between 50-60 different security products and solutions deployed. Covering the entire security spectrum – intrusion prevention, anti-malware, network and user behavior analysis, WAF, and more – these products generate hundreds or thousands of alerts on a daily basis, creating quite a few challenges.
• Each security vendor uses a different technology, resulting in different type of alerts and making it difficult to keep up with the required talent and expertise.
• Solution are delivered as stand-alone silos. With no integration between products’ security functions, effective contextual analysis is simply not possible.
• The large number of tools, as well as the need to constantly maintain policies up to date, increase the potential for misconfigurations or outdate policies, creating a false sense of security.
• The typical, siloed IT organizational structure makes it difficult for SOC teams to enforce the required actions, when most of the actionable network operations are under the responsibility of different groups.
This siloed security structure presents an opportunity for advanced attack campaigns. While SoC teams are occupied sifting through endless alerts and logs, with no real-time visibility and understanding of the “big-picture”, attackers can exploit dead spots and misconfigurations to sneak between security policies.
If you take a look at STIX, the collaborative effort to characterize cyber threats and specify attack, you’ll notice that attacks span across security functions. In the Target breach, more than 11 steps were taken by attackers.
Security Silos Breakdown – 4 Approaches
Recently I had the opportunity to speak to several CISO at large enterprises and Telco’s. Here are four possible methods that came up during our talks for addressing vulnerabilities resulting from security silos.
1. Consolidating security solutions using a small number of vendors. The idea is that by having less vendors, some of the issues mentioned above may be solved, since products arriving from a single vendor are better integrated. However, this approach is rejected by many CISOs since they don’t like to “color” their entire network with one or two vendors. A vendor-lock has some obvious and serious disadvantages for any organization. Personally, I tend to agree with this argument.
2. IT fusion. This is a promising initiative that aims to consolidate different IT groups such as network operations, applications security, Netsec teams, SoC, Audit, and others. Uniting multiple groups into a single entity can results in more coordinated and efficient work with faster response times.
3. Orchestration and automation systems. While the IT fusion strategy is a good one, it cannot help on its own to cope with advanced attack campaigns. It must be supported by orchestration and automation tools that enable executing security actions across the network. Such systems also amplify the investments already made in existing security infrastructure by most the large enterprises.
4. Aligning security policies with intent. Orchestration and automation is a great efficiency improvement, yet if security policies are misconfigured, they will not help much. Automation should be complemented with the ability to analyze and cover gaps or security holes between security intent and the policies of each security product.
For example, point of sales elements should be examined with a security policy focused on memory scarping malware and network data-leak behavior patterns, and less on DoS, brute force, social engineering and probe activities. Or another example – customer facing web services should be examined via policies focused on brute-force, DoS and injection type attacks, and less on social engineering, data-leak network patterns etc.
Organizational and security product silos are not likely to disappear anytime soon. As security professionals our first step is to recognize the vulnerabilities they create, and then select the appropriate methods to gain insight, fill in the gaps and be able respond quicker to minimize risks. We should ensure that the IT fusion strategies implemented in larger organization are supplemented with technologies that will allow them to succeed.















