Application Whitelisting and Change Policy Management Ensure that Data and Applications are Protected
Today’s cyberspace is often compared to the Wild West, with good reason. Criminal gangs roam around a vast, untamed wilderness. Cattle rustling has been replaced by identity theft. And, sometimes, just for kicks, today’s cyberscum deny services or destroy infrastructure—the modern-day equivalent of getting drunk and shooting up the town.
 Most of us in the IT industry are old enough to remember simpler times when the only thing you had to worry about was the occasional tech-savvy juvenile delinquent trying to mess with your Web site. Sure, sometimes you would have to discourage end users from opening email attachments from a “barrister” or “lottery official” notifying them about a million-dollar windfall in a foreign bank account. But that was it. Enterprises simply required spam filters, encryption, and basic anti-virus solutions. The set-up was primitive, but it worked.
Most of us in the IT industry are old enough to remember simpler times when the only thing you had to worry about was the occasional tech-savvy juvenile delinquent trying to mess with your Web site. Sure, sometimes you would have to discourage end users from opening email attachments from a “barrister” or “lottery official” notifying them about a million-dollar windfall in a foreign bank account. But that was it. Enterprises simply required spam filters, encryption, and basic anti-virus solutions. The set-up was primitive, but it worked.
Fast forward to 2011. Criminal syndicates are taking advantage of any opening, and their destructive powers are virtually unlimited. Consider what the Stuxnet worm did (and is still doing). Sure, it’s nice that, by causing centrifuges to spin out of control, Stuxnet set back the Iranian nuclear program by months or years. But Stuxnet is still out there wreaking havoc on legitimate industrial control systems the world over.
What’s worse, other more recent malware infections are pushing Stuxnet out of the headlines. Night Dragon, for example. It’s malware that is targeting global oil, energy, and petrochemical companies with the apparent intent of stealing operational details, exploration research, and financial data related to new oil and gas field bid negotiations. The breach of Sony’s online game network is another big one. It took place in April and resulted in the loss of names, addresses and possibly credit card numbers associated with 77 million accounts.
Clearly, cybercrime is a huge growth industry. Check out the bar graph below.
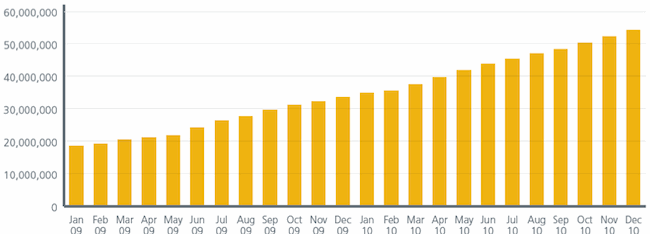
Figure 1: Total count of unique malware (including variants) Source: McAfee Labs
Note the upward trajectory. Cybercrime isn’t just on the rise, it’s skyrocketing. Of the nearly 55 million pieces of malware McAfee Labs has identified and protected against over the past 15 years, 20 million pieces were written in 2010 alone. That’s 36 percent of the total in one year! And 2011 looks like it’s going to be another banner year. It’s no wonder that AT&T’s Chief Security Officer recently told the U.S. Senate Commerce Committee that more money is being made from cybercrime than from drug trafficking.
Aside from security issues, the enterprise computing environment is getting tougher because, despite huge processor performance gains and the widespread adoption of virtualization and cloud computing technologies—or maybe because of them—CPU cycles are becoming increasingly scarce. They are rare commodities due to the proliferation of big, complex workloads as well as exploding demand for data in all its media-rich forms. Every aspect of our economy depends on CPU cycle availability right now. The upshot is, servers and endpoints must use those cycles efficiently. In many cases, these systems can’t be expected to handle the overhead of traditional security software anymore—especially fixed-function devices, embedded devices, POS terminals, and mobile devices.
Yes, times have changed and, by necessity, security technologies are changing too. Whenever possible, security concerns are being met by a combination of application whitelisting and change policy management technologies. Whitelisting doesn’t permit the execution of any instruction set that has not been previously approved. Change policy management ensures that systems are administered in compliance with verified and approved procedures. For example, a policy that requires wireless communications on your company’s mobile devices to be encrypted at all times can be easily enforced at the server. No one except pre-authorized administrators can change the policy or the registry entry on the wireless entry ports.
Together, whitelisting and change policy management ensure that data and applications are protected with minimal impact to system performance and availability.
With these technologies in place, no matter what happens in the world around them, system configurations stay the same. The ATM can’t be reprogrammed to spit out money; the production-line robot can’t be instructed to etch, cut or weld a defect into a product; the database won’t accept a SQL injection. In every case, trusted applications, system components, executables, and administrators are identified and explicitly allowed. Everything and everyone else is denied by default.
Of course this may cramp some people’s style within the enterprise. But, with this solution in place, crooks can’t cause harm—even internal ones—and human error is no longer a factor. The enterprise computing environment becomes like a frontier outpost in the old West where the money sacks and gold are locked away in the vault, the saloon is boarded up, and weapons are confiscated at the edge of town. Power remains in the hands of the sheriff—the chief security officer, if you will—and nobody steps out of line.
Traditional IT security remains essential, as it’s all about comprehensively, proactively managing risk. In addition, real-time, cloud-based threat intelligence services must continue to study and track the bad guys while alerting security officials in the private sector and government agencies whenever danger levels rise. But traditional IT security must evolve to the point where whitelisting and change policy management are pervasive. These technologies are the wave of the future. The only alternative is to wave a white flag.













