IE, Windows UMC Vulnerabilities Fueled Microsoft’s 2015 Patch Efforts
Microsoft patched more than 570 vulnerabilities in its products in 2015, the most of which affected the Internet Explorer (IE) browser, according to analysis from ESET.
ESET researchers sifted through vulnerability data gathered throughout 2015, and have created a report (PDF) to provide a look into the most affected components in Windows and to help increase user awareness on the importance of patching.
Following IE, various user mode Windows components (Windows UMC) saw the most resolved flaws, ESET said, and Microsoft Office ended in third place on the list.
According to the numbers, four times more Windows UMC vulnerabilities were patched in 2015 when compared to the previous year, and Office received more than two times the number of fixes compared to 2014. The number of IE vulnerabilities fixed in 2015 dropped slightly year-on-year.
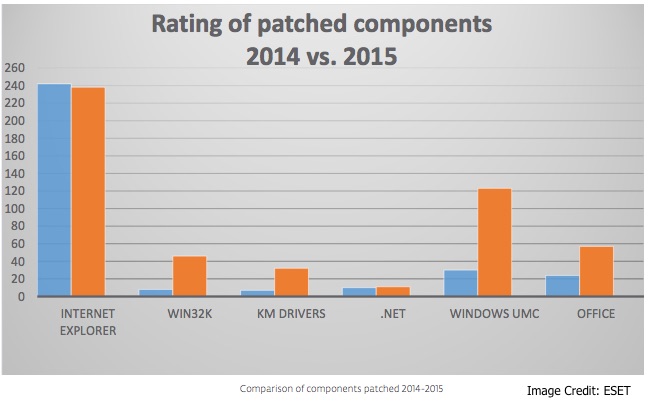
Other Windows components that saw a significant increase in patches include kernel mode (KM) drivers and the win32k.sys kernel component of the Windows GUI, both of which are targeted by attackers looking to gain system privileges on a victim’s machine. By exploiting these vulnerabilities, attackers can remotely execute code directly in kernel mode and can gain control of PC’s resources.
A Mount Manager Local Privilege Escalation (LPE) Vulnerability (CVE-2015-1769) was one of the most important LPE vulnerabilities fixed last year, found to affect all client and server editions of Windows from Vista onward. By exploiting it, attackers could run arbitrary code from a removable USB drive with system privileges.
Located in the system driver http.sys on Windows 7 and later, CVE-2015-1635 was another serious flaw resolved in 2015. The flaw could allow attackers execute malicious code remotely with system privileges, launch DoS attacks, or to bring down a targeted system with a Blue Screen of Death (BSoD).
Another important threat to Windows systems in 2015 was the Hacking Team breach, which resulted in leaked 0day exploits for Windows, Flash Player and Internet Explorer that could be used in specialized tools such as Exploit Kits to gain high infection rates.
In fact, Italy-based Hacking Team provided its customers with the ability to deploy backdoors not only on Windows machines, but also on Linux, Android, OS X, and iOS devices. Furthermore, it was revealed that exploits for Flash Player were meant to work for IE and Edge, Google Chrome, Mozilla Firefox, and Opera, and to affect Windows, Linux, and Apple OS X machines, the report shows.
Some browsers have implemented a series of counter measures to prevent attacks, such as Google Chrome and Microsoft Edge. For Chrome, the “PPAPI win32k lockdown” option allows users lockdown win32k for Flash/PDF plugins or for all render processes, as well as special checks and a new type of heap allocation to protect Flash Player process from buffer overflows.
Microsoft Edge, on the other hand, is protected against binary injection, courtesy of an option that prevents DLLs from being loaded into the browser unless the library is signed with a Microsoft digital certificate or with a Windows Hardware Quality Lab (WHQL) certificate from Microsoft.
With many of the Windows flaws that Microsoft patched in 2015 being 0day vulnerabilities, and with exploits already used in attacks to compromise systems, users must understand the importance of installing security updates in a timely manner.














