An analysis conducted using Mozilla’s Observatory tool has showed that modern security technologies are increasingly used by Alexa top 1 million websites.
Observatory, a free and open source tool developed by Mozilla Information Security Engineer April King, was announced in August 2016. The tool is designed to allow website developers and administrators to determine if they are using available security technologies at their full potential.
Observatory grades websites based on their use of security technologies such as Content Security Policy (CSP), Contribute.json, cookies, cross-origin resource sharing (CORS), HTTP Public Key Pinning (HPKP), HTTP Strict Transport Security (HSTS), redirections, subresource integrity, and X-Content-Type-Options, X-Frame-Options and X-XSS-Protection headers.
When the tool was first launched, King pointed out that usage rates of modern defensive security technologies were very low. A few months later, Observatory showed some improvements and the most recent data also shows an upward trend in the adoption of these technologies.
For example, the number of Alexa top 1 million websites using CSP has increased by 125 percent since April 2016. The number of sites using HTTPS has also increased by 36 percent, or roughly 119,000 websites, over the same period.
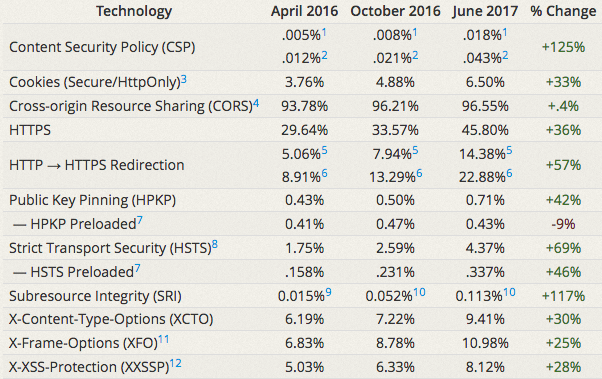
King pointed out that the increasing use of CSP is surprising, especially since the technology is not easy to implement on both new and existing websites.
According to King, more than 50,000 websites used the Mozilla Observatory to assess their level of security and over 2,500 of them have improved from a failing grade to an A or A+. Over 27,000 sites previously rated F got better grades in the past 8 months.
However, while there have been significant improvements, more than 93 percent of sites scanned using Observatory still received an F as of June 2017. Only less than one percent of the world’s most popular websites received an A+, A or B grade.
Related: Mozilla Revamps Bug Bounty Program
Related: Mozilla Wants 64 Bits of Entropy in Certificate Serial Numbers
Related: Mozilla Tells Symantec to Accept Google’s CA Proposal














