Mozilla announced on Thursday that it has relaunched its web security bug bounty program. White hat hackers are now provided clear information on how much money each type of vulnerability can earn them.
Mozilla has been running a bug bounty program since 2004. The organization initially rewarded only vulnerabilities found in its software, but in 2010 it expanded the program to include web properties.
The organization says it has paid out more than $1.6 million since 2010, but it has experienced some issues in communicating what types of flaws and which online properties are considered the most problematic.
“A hypothetical SQL injection on Bugzilla presents a different level of risk to Mozilla than a cross-site scripting attack on the Observatory or an open redirect on a community blog,” explained Mozilla security engineer April King. “To a bounty hunter, the level of risk is often irrelevant — they simply want to know if a class of bug on a specific site will pay out a bounty and how much it will pay out.”
Mozilla has decided to expand the list of websites and bug classes covered by its bug bounty program, and it now aims for greater transparency by providing more detailed information on payouts.
For instance, a remote code execution vulnerability in a critical website can earn bounty hunters $5,000, while an authentication bypass or a SQL injection can be worth up to $3,000. Cross-site request forgery (CSRF), cross-site scripting (XSS), XML external entity (XXE) and domain takeover flaws affecting critical sites can receive a payout of up to $2,500.
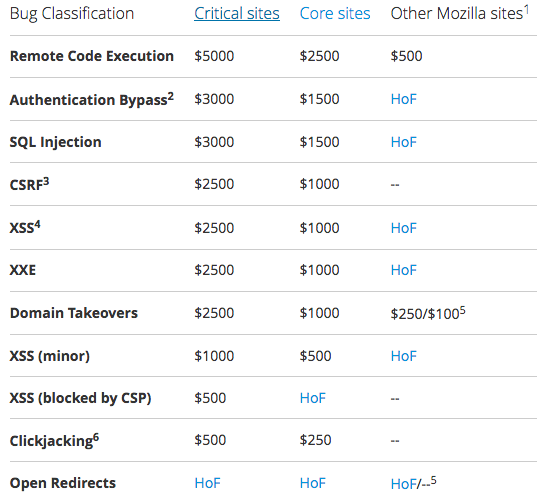
Critical properties include the main Firefox and Mozilla websites, and domains related to services such as ABSearch, add-ons, Bugzilla, crash reports, downloads, Firefox-related services, Push, Shield, Test Pilot, tracking protection and source control.
“Having a clear and straightforward table of payouts allows bounty hunters to devote their time and effort to discovering bugs that they know will receive a payout. The hunters will also know the exact amount of the payouts,” King said.
In addition to expanding the list of properties eligible for monetary rewards, Mozilla informed users that there are some new bug classes that can qualify for its bug bounty Hall of Fame.
Related Reading: Mozilla Patches Firefox Flaw Disclosed at Pwn2Own
Related Reading: Mozilla Wants 64 Bits of Entropy in Certificate Serial Numbers
Related Reading: Mozilla Launches Website Security Testing Tool












