Vectra Integrates Cognito with Microsoft Defender ATP and Azure Sentinel to Form a SOC Visibility Triad
San Jose, Calif-based threat detection firm Vectra has integrated its network threat detection and response (NDR) Cognito platform with Microsoft Defender and Microsoft Azure Sentinel to deliver Gartner’s concept of the SOC Visibility Triad.
Gartner introduced the idea of the SOC Visibility Triad in March 2019. The name is an allusion to the ‘nuclear triad’ of the Cold War: bombers, ICBMs, and missile-carrying submarines. Translated to SOCs, Gartner’s concept of the SOC visibility triad requires the integration of SIEM/UEBA, network detection and response (NDR), and endpoint detection and response (EDR).
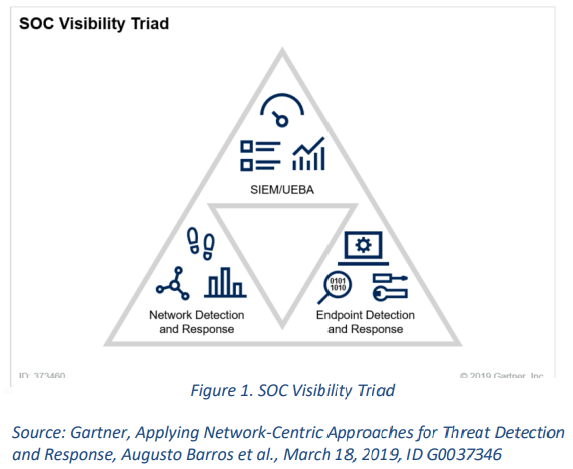 The SIEM/UEBA solution (in this instance, Azure Sentinel) can collect and analyze logs generated by the IT infrastructure — but does not analyze the network traffic. The EDR (in this instance, Microsoft Defender) can capture malicious activity on the endpoints — but loses track of the effect of the compromise on the overall network.
The SIEM/UEBA solution (in this instance, Azure Sentinel) can collect and analyze logs generated by the IT infrastructure — but does not analyze the network traffic. The EDR (in this instance, Microsoft Defender) can capture malicious activity on the endpoints — but loses track of the effect of the compromise on the overall network.
The NDR (in this instance, Vectra Cognito) can detect suspicious activity in the network traffic. However, in isolation, these three concepts lack context for their alerts, and leave the SOC team to triage a large number of alerts that may or may not be related, and may or may not be significant in isolation.
The new native integration between Vectra’s Cognito and Microsoft’s Defender and Sentinel is designed to provide the SOC with full oversight of the state of the infrastructure, and better ability to respond to suspicious events. If an endpoint is compromised, suspicious activity on other devices communicating with that endpoint can be analyzed. Other assets communicating with the endpoint’s C&C server can be detected, and unexpected use of a user account on other devices can be checked.
Jitin Dhanani, senior director, business development at Vectra, explains, “Through this collaboration with Microsoft, our customers will see immediate results without the workload that comes with embedded security silos. Ultimately, this combined effort will result in well-coordinated responses, enhancing the efficiency of their security operations, and reducing the attacker dwell times that drive risk for the business.”
Benefits from Cognito’s integration with Defender are expected to include fewer visibility gaps by combining Vectra’s aerial view of the network with Defender’s in-depth process-level view, providing the SOC team with the information necessary to pinpoint attackers, and the ability to take surgical action against those attackers closer to the source.
Benefits from the integration with Sentinel will include bringing Cognito detections straight to the Sentinel Workbook for immediate attention and deeper analysis, automating incidents, and the ability to perform forensic analysis on incidents to identify devices, accounts, and attackers involved.
“Vectra’s integration of Azure Sentinel and Microsoft Defender ATP will help further empower our customers by allowing them to reduce cyber noise and focus on the most complex issues and threats,” comments Mandana Javaheri, global director, Cybersecurity Solutions Group at Microsoft Corp. “The complete visibility combined with high fidelity attacker behaviors detections helps significantly strengthen our customers security posture.”
Microsoft has invited Vectra to become a member of The Microsoft Intelligent Security Association, an ecosystem of independent software vendors purpose-built to defend against increasing cyber threats.
Vectra was founded in 2010 by James Harlacher, Marc Rogers, and Mark Abene. It raised $36 million in a Series D funding round in February 2018, and a further $100 million in a Series E round in June 2019, bringing the total raised to date to $222.5 million.
Related: Reconnaissance, Lateral Movement Soar in Manufacturing Industry
Related: Cyberattacks Against Energy Sector Are Higher Than Average: Report
Related: The Intruder’s Kill Chain – Detecting a Subtle Presence















