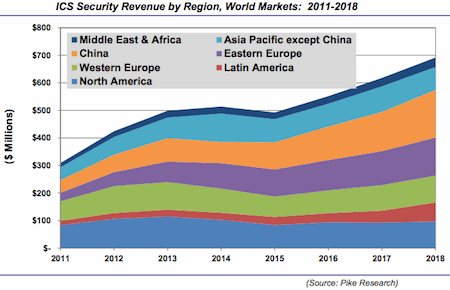
According to a new report published by Pike Research, a market research and consulting firm that provides analysis of global clean technology markets, increasing risks to the electrical grid will require utilities to make significant new investments in cyber security for industrial control systems (ICS), which the firm forecasts will total $4.1 billion between 2011 and 2018.
With electrical grids now often controlled by systems running Windows or Linux, and using IP networks to communicate, a new world of risks has been introduced, as the systems are no longer isolated within the perimeter of facilities. Wireless and Bluetooth capabilities are starting to appear in supervisory control and data acquisition (SCADA) devices that are integral to the backbone of grid operations.
Related Reading: Demystifying Industrial Network Security
“The smart grid changes everything, but when it comes to cyber security issues, much of the story remains the same,” says senior analyst Bob Lockhart. “Integrating information technology into a power grid presents enormous potential to deliver energy more efficiently and profitably, but also brings inherent risks in terms of security vulnerabilities. The discovery of the Stuxnet worm in 2010 shone a bright light on the fragility of industrial control systems such as SCADA, and has created a new urgency among security vendors and utility managers alike. Nearly overnight, ICS security went from being a non-issue to being critical.”
Lockhart adds that industrial control system security initiatives will include major investments in control consoles and systems, telecommunications security, human-machine interfaces, and sensors and collectors. The ICS security enhancements will serve key grid operations application areas such as distribution automation, substation automation, and transmission upgrades.
Related Reading: The Increasing Importance of Securing The Smart Grid
Pike Research’s analysis further indicates that smart grid deployments are not globally uniform, and thus some technology upgrades have been addressed earlier than others. For example, utilities tend to mitigate risks in transmission grids first, because a single outage in transmission can have such a wide-ranging effect. Pike Research’s report, “Industrial Control Systems Security”, analyzes and forecasts the market for ICS Security for Smart Grids, with an assessment of the major risks facing smart grid ICS environments. Risks were identified through a combination of primary research and mapping the environments against key security baselines such as NIST Special Document 800-82, Guide to Industrial Control Systems Security, and ISO27002:2005, Information technology – Security techniques – Code of practice for information security management.
Related Reading: Bridging the Air Gap: Examining Attack Vectors into Industrial Control Systems













