The year was 1983; Microsoft released Microsoft Word, McDonald’s introduced the Chicken McNugget and arguably the most significant development for the Internet occurred – the implementation of the Domain Name System or DNS. Without the DNS, it is doubtful the Internet could have grown and flourished as it has. Every time we receive or send e-mail, access a web page, make a Voice over Internet Protocol (VoIP) call, or complete many other tasks involving the Internet, we use the DNS.
As the Internet has facilitated and encouraged connections, it has in turn led to another important development: the evolution of the extended enterprise. As businesses have moved most of their operations online, from payment transactions to e-mail to content, they have turned for help to a web of partners: Software as a Service (SaaS) vendors, payment systems providers, Internet service providers (ISPs), etc. These organizations, collectively known as an extended enterprise, have become an essential framework for conducting business online. The extended enterprise even stretches into peoples’ homes, as e-commerce and online banking are now conducted on customers’ own computers. However, in order to have this interconnected ecosystem work without a hitch, it is crucial that the DNSs of these organizations and companies remain consistent and secure.
A Trust-Based System Evolves
In 1983, Jon Postel and Paul Mockapetris from the University of Southern California Information Sciences Institute devised a new way of assigning and recording Internet addresses with the distributed DNS. Their solution was revolutionary, because although it still used an underlying system of numerical designations, it allowed people to reach a computer by name as well. It was also hierarchical and distributed. Top-level domains would mark out various types of users, like .mil (military organization) or .edu (educational organization).
When these two (with the help of many others) created DNS, it was designed to be helpful and it was based on trust. It now serves as the pivotal technology that enables all Internet transactions to occur. Essentially, DNS is the directory assistance between a web site and an IP address connecting everything and everyone – trusting that people and organizations are who they say they are.
When DNS was first implemented, there was little incentive and information available for criminals to target the Internet for illegal activity. Today, however, the DNS protocol stores the location of more than a billion web addresses and routes nearly every piece of Internet traffic in the world – web sites, e-mail, instant messages, financial transactions, file sharing, etc. – making it an extremely lucrative target for cyber criminals.
Over time, as use of the DNS has exploded, so has the exploitation of its rudimentary setup. The most glaring example of this is DNS cache poisoning, which has gained notoriety recently with the discovery of a fundamental flaw in how DNS was designed. Cache poisoning is the corruption of an Internet server’s DNS table via the replacement of a legitimate Internet address with another “rogue” address. When a web user seeks the page at the legitimate address, the request is redirected by the rogue entry in the table to a different address. At that point, a worm, spyware, web browser hijacking program, or other form of malicious software (malware) can be downloaded to the user’s computer from the rogue location. But web site redirection is only part of the problem. Because DNS is used to control not only web sites, but also e-mail, instant messages, financial transactions, top-secret electronic data and more, if a domain’s DNS is poisoned, it could have a detrimental impact on the business itself, meaning cyber criminals could possibly gain access to all of this data.
Troubling Statistics
How widespread and damaging has DNS poisoning become? In January 2010, a poll by the security software company McAfee found that DNS poisoning attacks had occurred at 57 percent of the leading companies worldwide. Furthermore, according to the IT and security executives questioned, the cost of downtime incurred per company from a network infrastructure attack was more than six million dollars a day.
The United States Department of Homeland Security (DHS) issued a 114-page report in August of 2008 presenting several scenarios where well-chosen attacks against key IT infrastructure elements could cause disruptions on a national scale. In it, the DHS warns that the web site directory system is the most vulnerable to attack. Taking that a step further, the report says an attacker that utilizes holes in the DNS could take down a top-level domain such as .com (company) or .gov (government organization) – creating cascading effects on consumers, businesses and government entities that rely on such services.
For example, if a cyber criminal got access to .com’s generic top-level domain (gTLD), which is operated by VeriSign, it could essentially take over all .com domains. This could bring all of these organizations to a halt, while giving the criminal control of data/ e-mail/customers, etc. The trickle-down effect could be disastrous.
While it may seem unlikely that such a scenario could ever occur, we have seen instances of such attacks against some TLDs in recent months, either via hacks at the registry or against a domain registrar (e.g. New Zealand .nz and Puerto Rico .pr). It doesn’t even take a malicious attack to knock out large sections of the Internet’s infrastructure. Recently, the registry for Sweden (.se) mistakenly left off a single period in a critical file, rendering the entire TLD unreadable, effectively removing Sweden and all organizations within the .se space from the Internet for several hours.
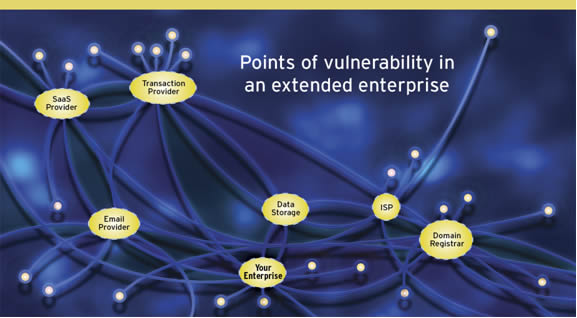
Extended Enterprise Enables Cyber Attacks from Multiple Angles
There are numerous instances where high-profile companies and organizations have become victims of DNS hijacking in the last couple of years. These include CheckFree, Comcast, Baidu, Twitter, and even the international oversight body for domain names itself, ICANN, By exploiting connections with partners, vendors, customers and other key players in an extended enterprise, hackers can and do gain access to the core transactions that facilitate business.
As more and more businesses move operations online, the importance of enterprise security increasingly extends to the extended enterprise. With today’s interconnected ecosystem, the biggest remaining security risk is not the enterprise, it is the enterprise’s partners: the SaaS vendors, payment systems providers, ISPs, outsourced services, etc. For example, enterprises forward customers to transaction providers to pay bills directly – tying their DNS in with the bill pay provider. By doing this, organizations often expose their clients to further dangers “outside their walls.”
In the case of CheckFree, the nation’s largest e-bill payment system, hackers were able to hijack the company’s domain names by stealing the user name and password needed to make account changes at Network Solutions, CheckFree’s domain registrar. The hackers then logged in using these credentials, changed the address of CheckFree’s authoritative DNS servers, and pointed visitors to all of CheckFree’s domains to an Internet address loaded with malware and controlled by a server in the Ukraine. The hacker(s) exposed a significant number of the 24.7 million CheckFree customers to a web address that tried to install malware on their computers.
Criminals could have used the malicious software not just to access CheckFree’s vital data, but also to steal information from the hundreds of transaction partners that rely on CheckFree for their bill pay services. If a utility provider sent a customer to CheckFree directly from its web site to pay bills, that customer would be exposed to CheckFree’s fake DNS. CheckFree’s hijacked DNS was suddenly not just CheckFree’s problem, but also that utility provider’s problem. The same held true for the more than seventy percent of banks in the U.S. that tie their own online banking systems to CheckFree’s bill pay systems.
As a final insult, all e-mail for CheckFree’s domains was shut down as the DNS hijacking also affected the e-mail server configurations controlled by DNS. This meant no one could send e-mail to CheckFree to alert them or find out what was occurring. A more determined attacker could have intercepted all of CheckFree’s e-mail during the take-over, exposing all of CheckFree’s customers and partners to further risk of loss.
Although CheckFree was able to regain control of its domains within about eight hours, the nature of DNS meant that the malicious server was still having traffic directed to it for up to forty-eight hours after CheckFree regained control of its domains.
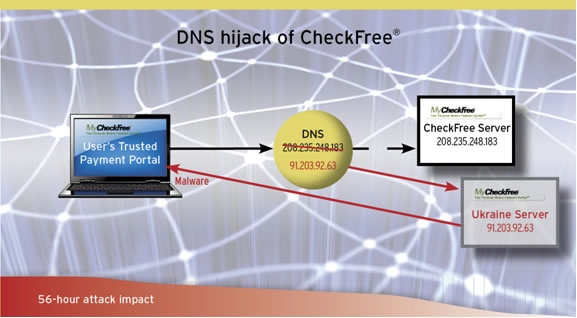
When a hijack or hack takes place, time is of utmost importance due to DNS caching. If a DNS entry is hacked (like with CheckFree), the distributed nature of the DNS system helps the false entries spread and dig in around the world like a virus at ISPs and enterprises, all of which cache DNS settings. The very nature of TTL (Time to Live) caching settings, which are intended to make the Internet more stable, means that corrections can often take more than 48 hours to resolve. Time to live is exactly like it sounds. It is essentially how long a DNS record is cached or saved on a resolving domain server or router. If a DNS has a long TTL, any changes you make to a DNS entry (like redirecting to another server) can take hours if not days to update – meaning a bad DNS entry could take hours or days to get changed back to a good DNS setting.
A DNS poisoning attack in April 2009 on Domainz.net, the main DNS registrar in New Zealand that controls most .nz domains, led to major .nz domains being maliciously redirected. The local web sites of Google, Microsoft, Yahoo, Coca-Cola, and other big companies were redirected to defacement sites. Those sites and other local sites including PayPal, Nike, Dell, and Nokia, were redirected to sites that were black except for messages in hacker lingo saying that the sites had been hacked. These “partner” sites were not hacked, but because the cyber criminals broke into the registrar’s DNS, they essentially could control all of these other brands’ Internet transactions – from web sites to messaging ( e-mail, instant messaging, etc.) and more.
In these and many other instances, hackers obtained control over DNS with password-stealing malware, or perhaps via an employee who was tricked into giving those credentials away through a phishing scam. Other cases have involved the theft of usernames and passwords from the domain management systems themselves via basic hacking techniques like SQL injection attacks. That meant that even companies that had been extremely diligent in their own password protection policies were exposed to DNS takeovers anyway, simply because the registrar or registry had an exposure. A simple password was all that was needed to change the Internet lifeline for hundreds of companies. Even more disturbingly, that is how things remain for the vast majority of domain names in the world to this day.
Getting to the Root of Matters
Would you allow a provider to have unmonitored control over your domains and DNS servers – essentially the keys to your corporate castle? Most companies do just that, by not independently watching their own DNS entries at their registrars and DNS providers. By connecting directly to extended enterprise partners via their domains, they grant those providers potentially unsecured access to their own customers, e-mails, and transactions. If you are not monitoring their DNS, you could be opening yourself up to cyber criminal attacks not only directly through your partners, but through your partners’ partners and so on. That is why it is so important to secure your extended enterprise.
However, monitoring your extended enterprise is only part of the battle. Quick remediation of DNS issues and errors can chop off propagation literally at the root before bad data can spread to long-lived caches. This fact makes fast identification and remediation even more important. Therefore, getting to the root of where your DNS was poisoned, whether it is an ISP, domain name registrar, or DNS service provider is imperative. Otherwise, the fraudulent entries will spread throughout the entire network or even the entire Internet. Eradicating the poisoned network entries can be extremely difficult and literally take days.
Actions Speak Louder Than Words
As content and transaction partnerships become more prevalent, and more and more business is done over the Internet, the need for a secure Internet presence for the extended enterprise becomes essential. Because the first line of defense for Internet presence lies with the DNS, securing the Internet’s directory assistance is a critical security step any organization must take.
Specifically, an enterprise must monitor, alert and remediate for changes not only to its DNS, but also its partners’ DNS. If a company that utilized CheckFree for its bill pay services had realized that CheckFree’s DNS was being rerouted, it could have recognized the attack, contacted CheckFree to alert them, and shut off or reconfigured its own bill pay services immediately. Conversely, if CheckFree had been monitoring its DNS aggressively, it could have alerted its hundreds of transaction partners about the hijacking and resolved the situation for everyone almost instantaneously.
A Plan of Action
As with any threat, your DNS exposures must first be identified and scoped prior to implementing protective measures. In the case of extended enterprise DNS, the key assets of your own organization need to be identified and prioritized based on risk exposure. For example, domains for your transaction systems are more important than a product name domain used to redirect traffic to your main web site. You also need to take stock of your key partners. With whom do you perform automated financial transactions, exchange sensitive e-mails, or accept content onto your corporate web site? To whom do you send your customers via links or advertising campaigns? If the Internet presence for one of those partners were taken over by a criminal intending to steal e-mail, install malware, or intercept transactions, what impact would that have on your organization? These key partners need to be monitored to ensure their DNS is continuously configured as expected.
Once you know what is important, you need to lock your own domains down. Unfortunately, locking things down is not easy – very few registrars or outsourced DNS providers have implemented things like multi-factor authentication for access control, but options do exist. For example, a new program launched by VeriSign for .com domains provides a registry-level backstop to nameserver changes. Some providers do offer out-of-band confirmation of nameserver or DNS mapping changes too.
Beyond locking things down, you need to establish a monitoring program that watches for changes in DNS entries to unexpected values for your own key domains and your partners across your entire extended enterprise. When things go awry, you’ll be informed quickly and can start to take actions to mitigate the problem, whether that means fixing something in your own system, or shutting down access to a partner until they put their own house in order. It’s important to look for changes at both the registry level and the DNS servers themselves so you can understand the true nature of any problems. Watching key ISP resolvers is also a wise precaution in order to spot major cache poisoning or hacking attacks that could affect large portions of your customer base. If problems do occur, you need a contingency plan to remediate each type of problem and to communicate with any ISPs that have cached the wrong data so they can fix it quickly.
The DNS is trusted, but not trustworthy – time to change the equation
With continuing rapid expansion of the extended enterprise, securing the DNS requires immediate attention to maintain trust throughout the entire Internet ecosystem an organization relies upon. By mitigating the always changing, dynamic security threats within the DNS for the extended enterprise, organizations can concentrate on their work and consumers can make purchases without worry. The extended enterprise’s Domain Name System is risky business that has been ignored for too long.-RR
Rod Rasmussen is the president and chief technology officer for Internet Identity, a provider of technology and services that secure the Internet presence for an organization and its extended enterprise.













