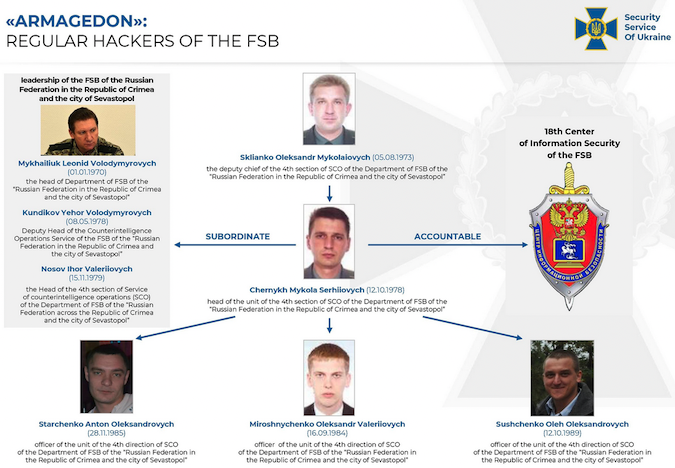
Ukraine’s security service, the SBU, on Thursday revealed the identities of five individuals allegedly involved in cyberattacks attributed to a Russia-linked threat group named Gamaredon.
According to the SBU, the five individuals are employees of Russia’s Federal Security Service (FSB). The names of the five and their role within the FSB have been made public, as well as recordings of phone conversations in which two of them appear to discuss cyberattacks.
The Ukrainian agency tracks the threat group that launched the attacks as Armageddon, but in the cybersecurity community it’s known as Gamaredon, Primitive Bear, Winterflounder, BlueAlpha, Blue Otso, Iron Tilden, Sector C08 and Callisto.
The threat group has been active since at least 2013, focusing on Ukrainian entities, including diplomats, government officials, journalists, military personnel, and NGOs. Cisco’s Talos unit reported earlier this year that Gamaredon appeared to be a hack-for-hire group that had been offering its services to other APT groups.
According to the Ukrainian security service, the hackers have carried out more than 5,000 attacks against Ukrainian entities, targeting critical infrastructure such as power plants and water facilities, harvesting classified information from government agencies, conducting misinformation campaigns, and disrupting IT systems.
The five FSB officers have been described as “officers of the ‘Crimean’ FSB, as well as traitors who sided with the enemy during the occupation of the peninsula in 2014.”
“The Ukrainian special service revealed the identities of the intruders, obtained incontrovertible evidence of their illegal activity, including interception of their phone calls. SSU has done it despite of the fact that the criminals used the FSB’s own malware, as well as means of anonymization and ‘covers’ in the Internet,” the SBU said. “Currently, 5 members of the hackers group received the suspicion notices of high treason according to art. 111 of the Criminal Code of Ukraine.”
The agency has published a 35-page report — written in English — that describes Gamaredon’s phishing attacks, exploited vulnerabilities, malware, command and control (C&C) infrastructure, and other TTPs.
Related: Ukraine Says Russian Cyberspies Targeted Gov Agencies in Supply Chain Attack
Related: InvisiMole Group Hits Military, Diplomats in Highly Targeted Campaign
Related: Russian ‘Gamaredon’ Hackers Back at Targeting Ukraine Officials