Many TLS certificates for .gov domains have not been renewed due to the ongoing shutdown of the United States government, making them insecure or inaccessible.
A standoff between U.S. President Donald Trump and the country’s Democratic Party over the controversial Mexico border wall has led to a partial government shutdown. The shutdown started on December 22 and it has entered its 20th day.
As a result, some government services, including ones related to cybersecurity, such as NIST’s Computer Security Resource Center (CSRC), are unavailable until further notice. According to Netcraft, the shutdown has also led to over 80 TLS certificates for .gov domains expiring without being renewed.
The expired certificates are for domains belong to organizations such as NASA, the Department of Justice, the Court of Appeals, and the Lawrence Berkeley National Laboratory.
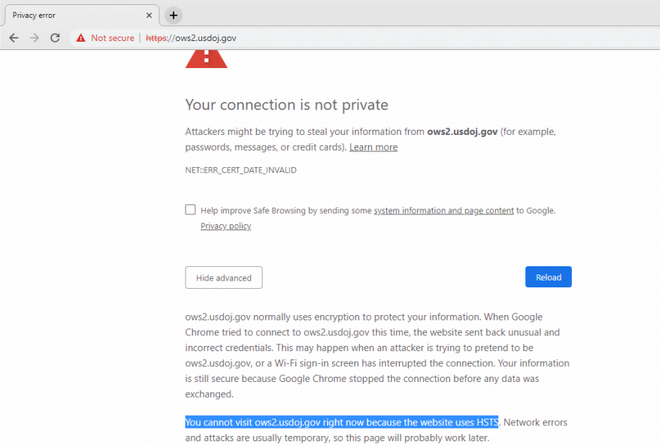
For example, the HTTPS certificate for ows2.usdoj.gov expired on December 17, just days before the shutdown, and it has not been renewed. When users try to access the website, they are presented with a warning that their connection is not secure due to the use of an invalid certificate.
Since usdoj.gov domains are on the HTTPS Strict Transport Security (HSTS) preload list, web browsers such as Chrome, Safari, Firefox, Edge, Internet Explorer and Opera prevent users from accessing them if their certificate has expired.
Websites that are not on the HSTS list can normally still be accessed by users as the browser’s “advanced” menu allows them to add an exception even if the security certificate is invalid. However, this option is not available for HSTS domains.
“Most of the affected sites will display an interstitial security warning that the user will be able to bypass,” explained Netcraft’s Paul Mutton. “This introduces some realistic security concerns, as task-oriented users are more likely to ignore these security warnings, and will therefore render themselves vulnerable to man-in-the-middle attacks.”
As an example of websites on which the security warning can be bypassed, Mutton provided rockettest.nasa.gov, for which the certificate expired on January 5, and d2l.lbl.gov, for which the certificate expired on January 8.
“As more and more certificates used by government websites inevitably expire over the following days, weeks — or maybe even months — there could be some realistic opportunities to undermine the security of all U.S. citizens,” Mutton said.
Related: Security of U.S. Government Sites Improved Only Slightly
Related: Many Federal Agencies Fail to Meet DMARC Implementation Deadline
Related: DMARC Use is Growing, But Difficult to Configure Correctly and Completely














