For many successful enterprises around the world, consultancy and advisory usage plays an important role in helping companies plan and execute, as well as overcome critical business challenges.
In areas such as human resources, public relations, accounting, marketing, legal and corporate strategy, companies often rely on domain-focused experts and services from outside their own walls.
Increasingly, the most effective kinds of advisories today now use tools and technology to stay so closely connected with an organization over time as to function almost as if they were an organic, internal department – but without all the overhead of “doing it yourself” or the crushing weight and cost of a big consulting firm or integrator.
Apart from being a high quality and very cost-effective alternative to developing expertise in-house, a cyber advisory approach usually lets companies be more effective, much faster, with better results.
Most importantly, advisories functioning in this manner allow companies to set a solid foundation for any given strategy area and then to regularly or continuously monitor progress against a plan, as well as adjust and execute with better agility; something that’s critical for dealing with unforeseen situations as they arise or in dealing with dynamically changing market or environmental conditions.
In other words, it’s a kind of continuous monitoring via a close advisory relationship and the right services, data and tools.
As cybercrime is now maturing into a formal business domain problem more than just a technical one, businesses can now benefit from applying this same sort of approach to their cyber defense strategy to fully realize the potential of all those expensive tactical defenses they’ve acquired.
What’s more, with the need for things like cyber threat intelligence (and the whole cyber intelligence domain in general) starting to get recognized more and more often in companies across industry as means to fill a big strategy gap in what has traditionally been a tactics-focused cyber defense approach, effective advisories can yield instant and long-term cyber resiliency benefits that make you safer, faster.
So what does a cyber intelligence advisory look like and how does it work?
It helps most to begin answering these questions by focusing on the challenges any cyber advisory must overcome to be of any value.
Whether it’s delivered as a service or combination of services and tools, to truly function in a pluggable way for most companies as something they can really use, a cyber advisory must overcome a big, pervasive obstacle across the whole of industry today:
In well over 90% of all cases that I’ve been involved with, most companies are not at present able (i.e. mature enough in their cyber defense and business management functions) to either stand up cyber intelligence operations themselves or take advantage of such information even if it existed.
In other words, when informed of a specific threat to a given part of their operations, most ask “So, what do I do now with this information?” Or, worse yet, “Who would even receive and act on this information inside my company in the first place?”
There are more than 50 million businesses in the United States today. Less than 1% of them are large businesses. As such, the vast majority of companies out there can’t even afford the dedicated budget and associated resources required to pursue even modestly robust cybersecurity.
Heck, even some of the most “well-to-do” of companies often skimp on cyber defense or simply don’t prioritize it sufficiently.
That means all the costly tactical lever pulling and button pushing continues to go on, year after year, without any guiding intelligence analysis and insight that helps inform more focused strategies, shorten response times, know what best practices to follow to mitigate a given vulnerability, prove diligence and responsibility for legal defenses or even simply where to go for help.
A cyber advisory can be a big help in fixing the problem by serving as highly-focused intelligence service “in a box” that businesses can use quickly to get bootstrapped and to use as the foundation for continuous monitoring of their risks to cyber threat in the future.
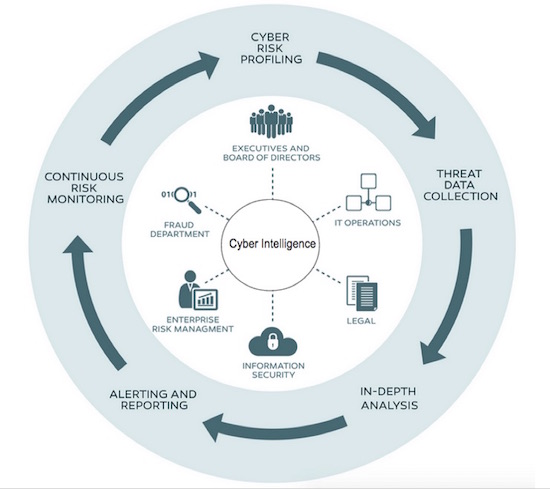
Companies should seek out advisory solutions that deliver the following as a combination of human expertise and tools:
Cyber Risk Profiling – The first step for any cyber advisor should be to gather information about what makes your company a risk. From info on your company’s industry and its subsidiaries, your mail and web domains, customer data being stored or transmitted, customer demographics to what’s on your IT baseline and what technologies support your customer’s web and mobile apps and more, an effective advisory knows you inside and out to enable highly-personalized threat detection that’s more than an overwhelming stream of “possibles” or “maybes.”
Threat Data Collection – In order to match your risk surfaces to new and existing cyber threats that could impact your business, any advisory solution must come with access to continuous and comprehensive data on cyber threats that can be made relevant to you. This data is more than virus or malware signatures, more than APT info or phishing data, it’s a full spectrum of threat data that informs on high and low level cyber threats from the Dark Web, to social engineering to data breach detection data.
In-Depth Analysis – Having cyber data is one thing. We all have data. Too much in fact, in the form of noisy alerts and indicators, log files, application outputs and so much more. Everything produces data. The key to a successful advisory is one that has a wealth of subject matter expertise that can also use practical intelligence and analysis methodologies that actually lead to real, effective defense actions.
Alerting and Reporting – Most companies are fractured when it comes to communicating even typical, run-of-the-mill information such as sales data. They’re even more stovepiped and disconnected when it comes to cyber threat information. A good advisory will not only profile your company’s risk, gather threat data, and perform practical analysis, but they’ll assist you with executing on timely and effective communication throughout your organization to those business units most likely affected by any given threat – and help them know what to do about it.
Continuous Risk Monitoring – In the business world today, threats come fast and furious. They’re dynamic from day to day. A useful advisory will recognize that company profiling, data collection, analysis, and alerting and reporting is something that needs continuous wash-rinse-repeat. In fact, a cyber intelligence advisory worth anything is one that’s always on and always monitoring your business risks for cyber threats as things evolve.
If you’re not now adding cyber intelligence to improve and enhance your tactical cyber defense strategy, you’re not alone. In fact, your reality is more the norm for about 50 million American business. For most, it’s something that’s simply out of reach resource-wise. Besides, even if you knew what was threatening you, you aren’t likely to know what to do about it.
Could your business use a cyber advisor? Can it afford not to?














