Tens of thousands of devices around the world, including many industrial control systems (ICS) and government computers, have been targeted in what appears to be an espionage campaign that involves a new piece of malware dubbed PseudoManuscrypt, Kaspersky revealed on Thursday.
The attacks targeted 35,000 devices in 195 countries between January and November 2021, including devices housed by high-profile organizations. Roughly seven percent of the targets were ICS, with the engineering and building automation sectors being most impacted. Attacks were also aimed at military industrial enterprises and research laboratories.
In many cases, the attackers targeted engineering computers, including devices used for 3D and physical modeling, which led Kaspersky researchers to believe that the goal may be industrial espionage. However, the company noted that the number of victims is large and it could not determine a clear focus on a specific type of industrial organization.
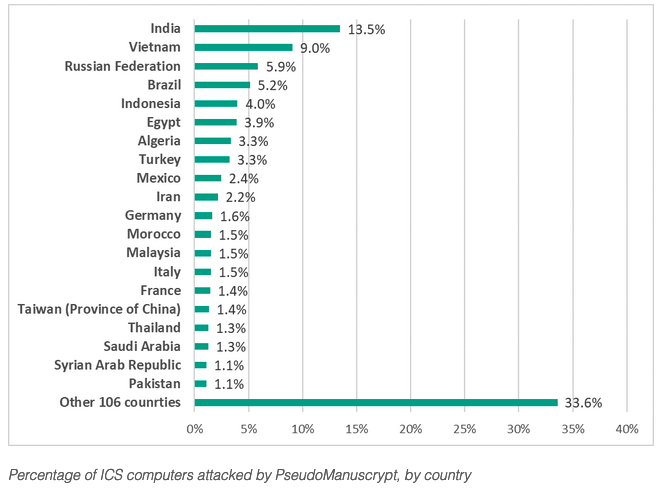
Nearly one-third of the non-ICS devices targeted in this campaign were located in Russia, India and Brazil. As for ICS, the highest percentage of targets was observed in India, Vietnam and Russia.
Kaspersky has dubbed the new spyware PseudoManuscrypt due to similarities to the Manuscrypt malware used by the North Korea-linked Lazarus group in attacks on the defense industry.
On the other hand, the malware uses the KCP protocol to connect to its command and control (C&C) server. The KCP protocol, whose use by malware is uncommon, has also been leveraged by the China-linked threat group APT41 in its attacks on industrial organizations.
The malware samples also contain comments written in Chinese, the malware connects to a cloud storage service offered by Chinese company Baidu, and the threat specifies Chinese as the preferred language when connecting to its C&C server.
However, Kaspersky said it cannot definitively link the PseudoManuscrypt campaign to Lazarus or any other known threat group.
The malware can steal VPN credentials, log keystrokes, capture the content of the screen (both images and video), record sound captured by the microphone, and steal clipboard and OS event log data.
PseudoManuscrypt has been distributed using pirated software installer archives — including ones related to ICS software — likely delivered by a malware-as-a-service platform. In some cases, the malware was delivered by the Glupteba botnet.
“Despite collecting and analyzing a large amount of data, it seems to us that many of our findings remain unexplained and do not fit any known schemes,” Kaspersky said. “Thus, we cannot say for certain whether the campaign is pursuing criminal mercenary goals or goals correlating with some governments’ interests.”
Related: Mac Malware Used in Attacks Targeting Industrial Organizations in Middle East
Related: Hundreds of Industrial Organizations Received Sunburst Malware in SolarWinds Attack















