Mozilla is working on addressing a Firefox bug that has been exploited by tech support scammers to lock the browser when users visit specially crafted websites.
Attacks were spotted recently by Jérôme Segura of Malwarebytes, who told SecurityWeek that there are currently two known Firefox bugs that have been abused in tech support scams.
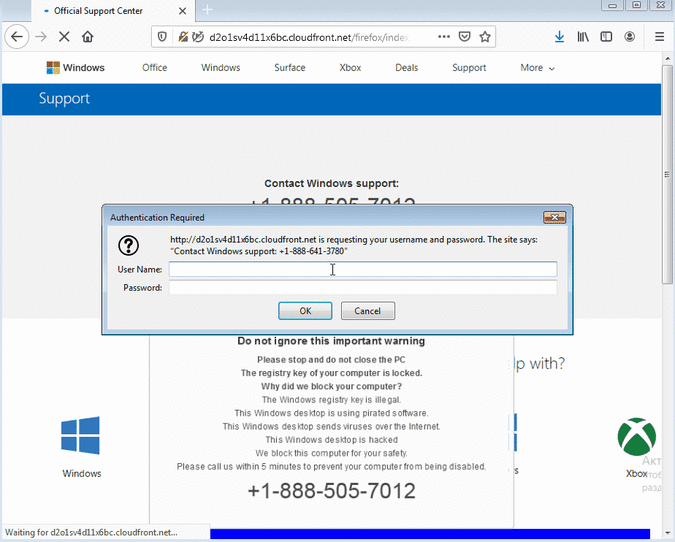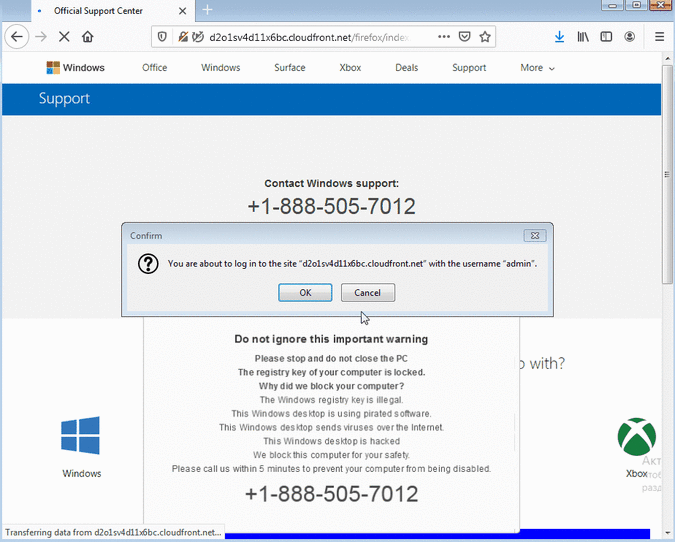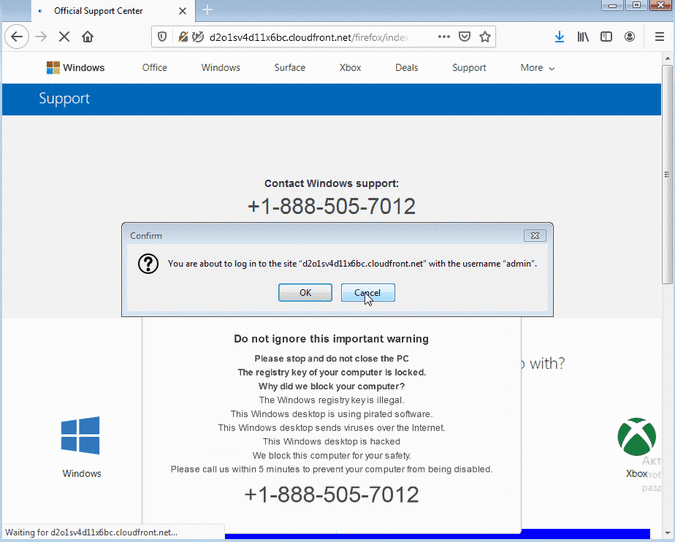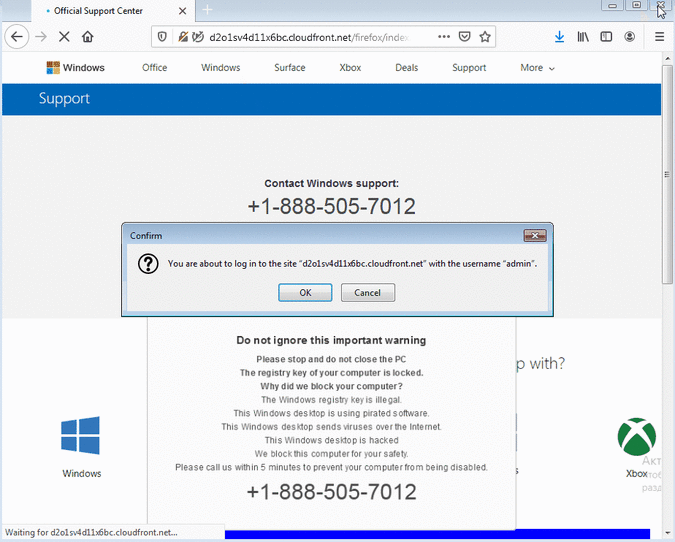
Exploitation only requires that users visit the websites set up by the cybercrooks. These sites display warnings and instruct victims to call “Windows support” at a specified number.
Segura informed Mozilla of one bug, which has the bug ID 1438214, two years ago, when a very similar flaw had been exploited by scammers against Chrome users. The flaw allows an attacker to freeze the browser by exploiting the download blob API in a way that consumes all CPU resources.
The researcher recently decided to revisit this bug and discovered that it remains unfixed. He also identified a newer bug that has also been exploited by tech support scammers.
“The newer bug abuses notifications by perpetually asking users for the same authorization,” Segura told SecurityWeek, explaining that this flaw appears to be a variation of a previously fixed issue that involved authentication pop-ups and which had been exploited for years.
Based on information in the new bug report created by Segura, Mozilla has known about this issue for at least three months — Mozilla developers flagged Segura’s report as a duplicate — but a fix has yet to be released.
Mozilla has not responded to SecurityWeek’s request for comment, but based on discussions in the bug reports, a patch is expected to be included in Firefox 71, which is scheduled for release on December 3.
Until a patch becomes available, users who encounter the scam websites can forcefully close Firefox from the Task Manager on Windows or using the Force Quit option on macOS — the bug affects Firefox on both Windows and macOS.
Related: Vulnerability Patched in Firefox Password Manager
Related: Firefox Zero-Day Vulnerability Exploited in Targeted Attacks













