Apache Tomcat Server Backdoor Worm Squirming
Malware hunters at Symantec have intercepted a malicious backdoor worming its way though servers running the open-source Apache Tomcat servers.
The backdoor worm, named Java.Tomdep by Symantec, acts as a Java servlet that is executed on Apache Tomcat. The malware does not affect client systems. Instead, it infects only the server and behaves as an IRC bot, connecting to an IRC server to send and receive commands sent from the attacker.
“Aside from standard commands such as download, upload, creating new process, SOCKS proxy, UDP flooding, and updating itself; compromised computers can also scan for other Tomcat servers and send the malware to them. It is thus possible that DDoS attacks from the compromised servers are the attacker’s purpose,” according to Symantec’s Security Response Team.
The malware uses weak usernames and passwords to worm its way through Tomcat servers. If successful, Java.Tomdep deploys itself to any Tomcat server it finds.
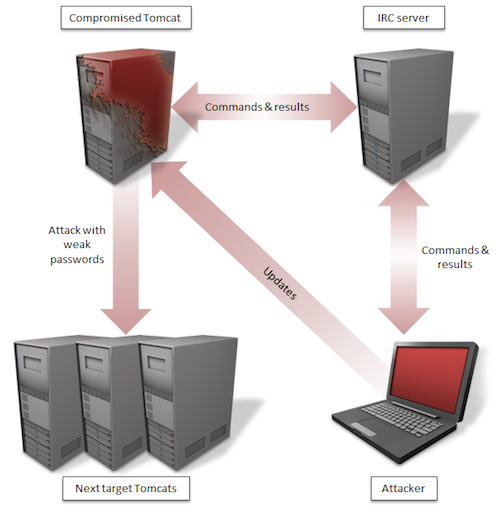
Figure 1: How Java.Tomdep Spreads (Image Credit: Symantec)
Symantec says the attacker’s command and control (C&C) servers are located in Taiwan and Luxembourg. Infected Tomcat servers have been spotted in the U.S., U.K., Brazil and China.
“As far as we know, not many computers have fallen victim to this threat yet. However, in some cases, server computers don’t have antivirus products installed on them in the same way that personal computers would. Hopefully this isn’t a reason for the low rate of detection,” Symantec added.
Related Reading: Attackers Hide Communication With Linux Backdoor
















