It was only a matter of time. When it comes to hit and quit scams, Rogue AV applications and Ransomware are rather cheap and easy to produce, and offer criminals a rather profitable mode of attack. Pay the fee, or lose access to your data.
On the desktop, Rogue AV applications tell the user that they suffer from some kind of infection, even when none exists, and demands registration before the threats (no matter how phantom they are) can be removed. In addition to scamming a person out of money, criminals are often paid by the install for these applications, earning a double payday. In the past, Rogue AV has also taken over a computer, preventing legit security applications from working properly, altering the desktop, and limiting Web access.
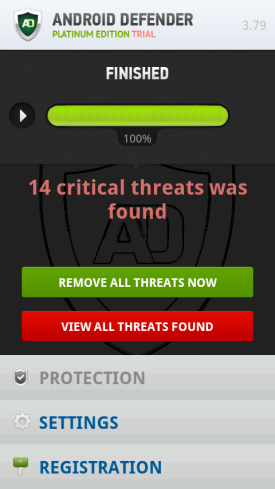 Likewise, Ransomware is also a pay per install program for many criminals. When Ransomware strikes, it encrypts valuable data, such as documents, spreadsheets, password databases, images, music, and more; demanding payments before the hijacked data is decrypted. Some Ransomware is poorly created, enabling security firms to prevent it from working or cracking the decryption keys. However, criminals have become clever – creating malware that totally locks the system, making it near impossible to crack.
Likewise, Ransomware is also a pay per install program for many criminals. When Ransomware strikes, it encrypts valuable data, such as documents, spreadsheets, password databases, images, music, and more; demanding payments before the hijacked data is decrypted. Some Ransomware is poorly created, enabling security firms to prevent it from working or cracking the decryption keys. However, criminals have become clever – creating malware that totally locks the system, making it near impossible to crack.
Now, researchers at Symantec have detected a new type of Ransomware. This one targets mobile devices, and comes masked as an anti-virus application. So what you have is a mix of both worlds, Rogue AV and Ransomware, combined to target a new platform – your phone.
“Once the malicious app has been installed, user experience varies as the app has compatibility issues with various devices. However, many users will not have the capability to uninstall the malicious app as the malware will attempt to prevent other apps from being launched,” Symantec explained in a blog post.
“The threat will also change the settings of the operating system. In some cases users may not even be able to perform a factory data reset on the device and will be forced to do a hard reset… If they are lucky, some users may be able to perform a simple uninstall due to the fact that the app may crash when executed because of compatibility issues.”
While the malware discovered by Symantec was only detected in a third-party app store and not on Google Play, the infection point is rather low. The point however, is that when it comes to mobile, what was once old has now become something new. The problem is, development methods of malware from a few years ago have been improved, so many of the methods for dealing with these threats on the desktop simply don’t apply to a mobile device.
Symantec detects this Android malware as Android.Fakedefender.
Symantec has a brief video explaining this malware which is embedded below.
















