The notorious Stuxnet malware is still actively running on some computers and while the threat cannot be controlled by the original attackers, its presence demonstrates the weak security posture of these organizations.
Stuxnet, reportedly developed by the United States and Israel, is a worm designed to target industrial systems. The malware became known as the world’s first cyber weapon after it caused serious damage at Iranian nuclear facilities.
Now, five years after it was first discovered, Stuxnet infections still exist, according to Czech Republic-based security firm Kleissner & Associates, which operates the botnet monitoring system Virus Tracker.
In a paper published last week, titled “Internet Attacks Against Nuclear Power Plants,” the company provided some Stuxnet-related statistics from Virus Tracker. Kleissner & Associates has the ability to monitor Stuxnet infections because it has acquired two of the command and control (C&C) domains used by the worm and pointed them to Virus Tracker sinkhole servers.
According to Kleissner, there were at least 153 unique machines infected with Stuxnet in 2013 and 2014. Nearly half of these infections were traced back to Iran, but some infected devices had also been spotted in India, Indonesia, Saudi Arabia, Kazakhstan and China. Experts determined that six of the infected computers had SCADA development software installed.
While these statistics are from 2013 and 2014, even today there are a few organizations that have failed to remove Stuxnet from their systems. Peter Kleissner, founder and CEO of Kleissner & Associates, told SecurityWeek that Virus Tracker shows more than 200 Stuxnet infection records in 2015.
India accounts for roughly 45 percent of infection records, followed by Iran with 33 percent, and Indonesia with 10 percent. Kleissner has pointed out that the number of infection records doesn’t indicate the number of unique infected devices because the same infection can generate multiple records.
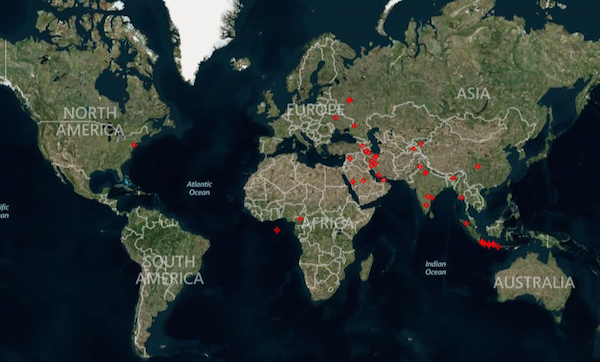
Kleissner noted that while the malware is still actively running in the background on these machines, it cannot be controlled by the original attackers because the C&C domains are owned by the security company. However, this shows that some organizations are not doing a good job when it comes to cleaning up malware.
The statistics presented by the security firm are meant to show that there is a risk of Stuxnet-like operations and that nuclear plants might not be difficult to breach.
“It is inevitable that existing malware infections lower the overall security of the particular machines and the entire networks and therefore make it easier (or possible at all) for anyone else to intrude the system,” reads Kleissner & Associates’ researcher paper. “Just as Kleissner & Associates’ C&C domain control enables us to control any remaining Stuxnet infected machines, any capable intelligence service (or individual with the knowledge and skills) could seize control and potentially cause considerable damage leveraging the remaining infections.”
According to the security firm, many nuclear facilities host administrative systems infected with common malware. Attackers can leverage access to these administrative systems to mount attacks on industrial control systems.
Virus Tracker shows malware infections at IP ranges that appear to belong to nuclear facilities, but experts cannot determine if the infected device is a worker’s laptop, a guest Wi-Fi, or a machine controlling the entire nuclear power plant. On the other hand, Kleissner has pointed out that any malware connecting from the facility to external C&C servers can be problematic.
Kleissner told SecurityWeek that they have identified Conficker B and Ramdo infections on IP addresses that appear to belong to an energy provider in the United States. Other examples include Conficker and Sality infections on IP addresses apparently associated with atomic energy research organizations in China and Korea.
















