New Solution Helps Enterprises Discover, Understand and Block Malware Utilizing Big Data Analytics
Sourcefire today introduced a new malware protection and analysis solution designed to work alongside traditional endpoint security solutions and help discover malware threats that may have been missed by existing endpoint defenses.
 Dubbed FireAMP, the new offering provides increased visibility and control to help discover and block threats missed by other security layers.
Dubbed FireAMP, the new offering provides increased visibility and control to help discover and block threats missed by other security layers.
“FireAMP is not anti-virus software,” explained Alfred Huger, VP of Development, at Sourcefire’s Cloud Technology Group. “The solution works in conjunction with deployed endpoint software, trying to help cover areas that don’t have coverage today.”
The solution analyzes and blocks malware by utilizing what the company calls “big data analytics”, and brings powerful reporting that delivers visibility into the state of malware in enterprise environments.
FireAMP reports identify and detail high-risk systems; threat root cause, showing applications that are introducing malware; and advanced persistent threats, listing advanced malware that could be unique to a customer’s environment. FireAMP also includes comparative reporting, so that users can evaluate activities within their environment in the context of their overall organization or the installed base of FireAMP customers.
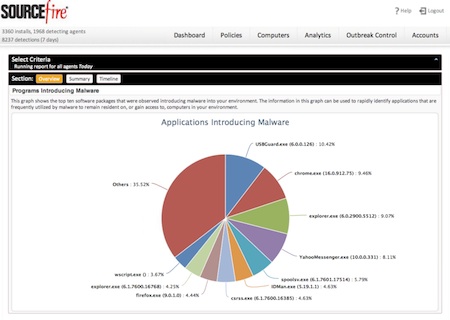 If a malicious file is discovered, FireAMP can help discover the spread of a file in the enterprise and prevent it from being spread further. “We want to take a customer and show them every single endpoint that experienced a file that they think is malicious,” Huger told SecurityWeek. “We want to tell them not only where malicious files have been, but where they came from, and what they did.”
If a malicious file is discovered, FireAMP can help discover the spread of a file in the enterprise and prevent it from being spread further. “We want to take a customer and show them every single endpoint that experienced a file that they think is malicious,” Huger told SecurityWeek. “We want to tell them not only where malicious files have been, but where they came from, and what they did.”
The solution marks the latest addition to the company’s portfolio of products designed to encompass its Agile Security vision for context-aware, adaptive and automated security solutions.
A breakdown of FireAMP’s capabilities include:
• FireCLOUD – Cloud-based infrastructure encompassing a number of advanced detection capabilities that leverage big data analytics to identify and score threats missed by other security layers
• File Trajectory – Tracks file movement within the enterprise, allowing organizations to identify the entry point and propagation path of malware
• File Analysis – Provides detailed information on malware behavior backed by the elite Sourcefire Vulnerability Research Team (VRT™) and the company’s collective security intelligence
• Outbreak Control – Customer-defined detections that block malware without requiring an update from your security vendor
• Cloud Recall – Continuous in-the-cloud analysis of historical file activity to discover and remediate threats that were previously missed
On the endpoint, FireAMP uses a lightweight kernel-based agent that connects to a cloud-based platform and only uses metadata to analyze files, requiring less storage and system resources than traditional endpoint security products.
“While developing this product, we spoke with more than 100 large enterprises and heard one common theme – while they have the latest security technologies with all of the latest updates, they still see malware infections,” said Oliver Friedrichs, senior vice president of Sourcefire’s Cloud Technology Group.
“Test results consistently show that the endpoint protection platforms currently available still do not protect endpoints against mass-propagated consumer threats — and their performance is even more dismal when faced with handcrafted targeted attacks,” said Neil MacDonald, vice president and fellow, and Peter Firstbrook, research director, at Gartner. “Gartner currently estimates that 4% to 7% of enterprise endpoints are infected at any given time, and that the next scheduled scan will catch only 1% of threats.”
FireAMP supports endpoints running Windows XP SP2+, Windows Vista SP2+, Windows 7, and Windows Server 2008.
Pricing starts at $30 per seat annually, and includes 24×7 technical support, maintenance releases and content updates, and access to the Sourcefire hosted FireAMP Management Console and FireCLOUD analytics platform.











