Several security firms have teamed up to analyze and potentially disrupt the activities of a threat group that is believed to be behind the 2014 attack on Sony Pictures Entertainment.
Novetta, Kaspersky Lab, AlienVault, and Symantec published reports on Wednesday on the activities of an actor they have dubbed the Lazarus Group. As part of what they call Operation Blockbuster, researchers from these companies have analyzed more than 45 malware families, which has allowed them to find connections between several major attacks and tie them to a single group.
The Lazarus Group has been active since at least 2009, but possibly as early as 2007, and it has conducted not only cyber espionage operations, but also attacks whose goal was to destroy data and disrupt systems.
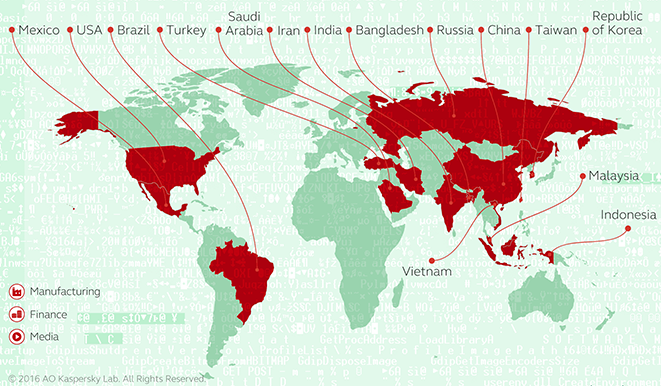
Based on the analysis of malware samples, experts have managed to link the Lazarus Group to numerous attacks, including the one that crippled and shamed Sony in 2014, the Dark Seoul and Operation Troy campaigns, and attacks on government, media, military, aerospace, manufacturing and financial organizations primarily located in South Korea and the United States. Victims have also been spotted in Taiwan, Brazil, Mexico, Turkey, Saudi Arabia, Iran, India, Russia, China, Indonesia, Malaysia, and Vietnam.
Researchers managed to connect these campaigns to Lazarus based on code shared between several malicious tools, and similarities in the attackers’ modus operandi, including methods used to wipe their tracks and evade detection by security products.
In December 2014, experts reported finding links between Destover, the wiper used in the Sony attack, and DarkSeoul malware, but experts had not found any conclusive evidence to link the threats to the same malware developers.
One key piece of evidence that has now allowed investigators to tie tens of targeted attacks that had been carried out by previously unknown actors to a single group was found in the malware droppers.
The analyzed droppers all stored their payload inside a password-protected archive file. The password set by the attackers was the same in every campaign and it was hardcoded inside the dropper. While this method was used to prevent automated systems from extracting the payload, it provided researchers the information they needed to identify Lazarus’ operations.
The U.S. government has pointed the finger at North Korea for the Sony attack and South Korea has blamed Pyongyang for many of the malicious campaigns targeting the country, but North Korea has always denied launching cyberattacks against the United States and South Korea.
The reports published by security firms on the Lazarus Group don’t directly accuse North Korea, but the evidence they present suggests that it could be responsible. For example, Kaspersky noted that the malicious tools used by the threat actor had been compiled during the working hours associated with the GMT+8 and GMT+9 time zones, which matches North Korea. Kaspersky also noted that more than 60 percent of Lazarus samples have at least one PE resource with Korean locale or language.
Novetta’s report presents evidence that the Sony attack was likely not the work of hacktivists or insiders, as some concluded shortly after the incident.
“This actor has the necessary skills and determination to perform cyberespionage operations with the purpose of stealing data or causing damage. Combining that with the use of disinformation and deception techniques, the attackers have been able to successfully launch several operations over the last few years,” said Jaime Blasco, chief scientist at AlienVault.
“As we predicted, the number of wiper attacks grows steadily. This kind of malware proves to be a highly effective type of cyber-weapon. The power to wipe thousands of computers at the push of a button represents a significant bounty to a Computer Network Exploitation team tasked with disinformation and the disruption of a target enterprise,” said Juan Guerrero, senior security researcher at Kaspersky Lab. “Its value as part of hybrid warfare, where wiper attacks are coupled with kinetic attacks to paralyze a country’s infrastructure remains an interesting thought experiment closer to reality than we can be comfortable with.”
Technical details on the Lazarus Group’s activities are available in the reports published by Kaspersky, Symantec, Novetta and AlienVault.
















