ATLANTA — SECURITYWEEK 2019 ICS CYBER SECURITY CONFERENCE — Some of the recent cybersecurity incidents involving industrial control systems (ICS) have resulted in injury and even loss of life, according to a survey conducted by Control Systems Cyber Security Association International (CS2AI).
CS2AI is a non-profit organization focused on the growth and expansion of networking opportunities and professional development of everyone involved in the field of control systems cybersecurity. The organization, which currently has over 16,000 members worldwide, is conducting a yearly analysis of the state of ICS cybersecurity through a survey that aims to help answer key questions on how critical systems can be best protected.
Roughly 300 individuals responsible for the cybersecurity of industrial and automation systems have already taken the survey and CS2AI will publish a complete report next month, but some of the data collected so far was presented this week at SecurityWeek’s 2019 ICS Cyber Security Conference in Atlanta. The survey can be taken at any time and the data collected after the first report is published will be used for the next report.
Some of the experts present at the ICS Cyber Security Conference pointed out that many industrial organizations still don’t take cybersecurity seriously, often arguing that they haven’t been or they are unlikely to be targeted by malicious actors.
However, the survey shows — assuming that the respondents answered truthfully — that OT security incidents can have serious consequences when they do occur.
When asked about the impact of ICS security incidents experienced in the past 12 months, roughly 1% of respondents admitted that it resulted in injury and 1% said the incident led to loss of life.
There is no additional information on this handful of incidents as the data was mostly collected anonymously — respondents are given the option to provide their information if they want to register for the opportunity to win a prize.
Approximately a quarter of respondents said the incident led to operational disruptions, and many could not provide an answer due to organizational policies.
Malware-infected removable media drives were named as an attack vector by 34% of respondents and nearly as many have named email (e.g. phishing). Sixteen percent have named hardware or software pre-infected with malware, 12% blamed third-party websites (e.g. watering hole attacks), and 10% blamed infected or compromised mobile devices for the incident suffered by their organization. Physical security breaches and Wi-Fi compromise have also been named by some respondents.
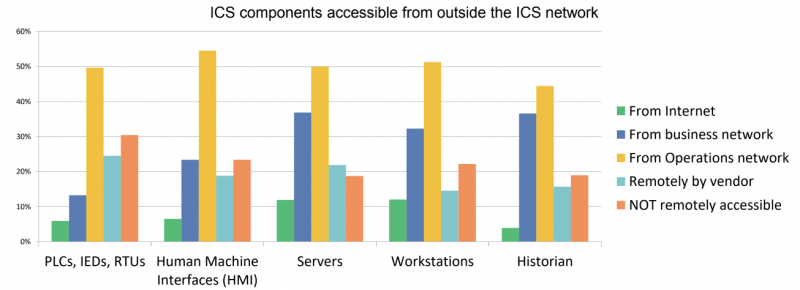
Some organizations have admitted having control systems accessible directly from the internet, including PLCs, HMIs, servers, workstations and historians.
Of all the respondents, 45% have an operational role, followed by individuals in management (20%), leadership (18%) and executive roles (17%). Nearly half of the respondents are from North America and a quarter are from Europe, with the rest representing the APAC, Middle East and Latin America regions.
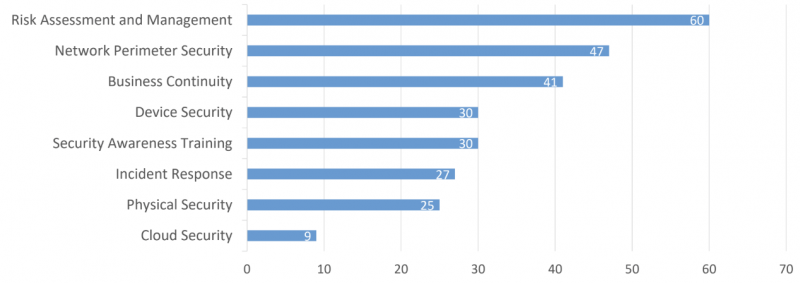
The top priority of many organizations is risk assessment and management, followed by network perimeter security, and business continuity. Cloud security is at the bottom of the chart and is a priority to only a handful of industrial organizations.
When asked about the obstacles in remediating or mitigating ICS vulnerabilities, the most common answer was insufficient expertise, followed by insufficient personnel, operational requirements (e.g. flaws cannot be addressed due to mandatory uptime), insufficient financial resources, and insufficient support from leadership.
The full report from CS2AI will also present data on spending and budgets, awareness training, organizational plans, cybersecurity programs, and security assessments.
Related: Outdated OSs Still Present in Many Industrial Organizations














