Researchers at AdaptiveMobile Security, a firm that specializes in cyber telecoms security, have disclosed a new SIM card attack method that could work against over 1 billion mobile phones, and they claim it has already been exploited by a surveillance company to track users.
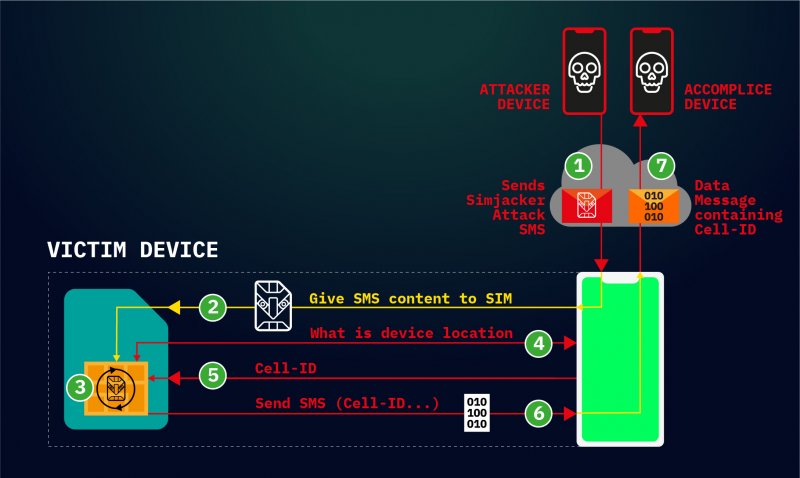
Dubbed Simjacker, the attack involves sending a specially crafted SMS message to the targeted phone. The message contains SIM Toolkit (STK) instructions and it’s processed by the SIM card (the universal integrated circuit card, or UICC), specifically the S@T Browser present on the SIM.
An attacker could use this method to send a wide range of STK commands to the targeted device, including for playing a tone, sending SMS messages, making phone calls, collecting information about the device (location, IMEI, battery, language), launching a web browser, powering off the card, requesting geographical location, and exfiltrating data.
These commands can allow the attacker to track a user’s location, send arbitrary messages on a victim’s behalf (including to premium-rate numbers for fraud purposes), spy on users, deliver malware by instructing the device’s web browser to access a malicious website, and cause a denial-of-service (DoS) condition.
According to AdaptiveMobile Security, an unnamed company that helps governments monitor individuals has been using the Simjacker method to track users for at least 2 years. The security firm says it has observed this surveillance company tracking hundreds of people in a single country through this method.
The spying company has targeted users in several countries, in some cases exploiting weaknesses in the SS7 protocol to achieve its goals in case the Simjacker attack fails.
The Simjacker attack is possible due to S@T Browser, a piece of legacy software originally designed for services that required interaction with the SIM card (e.g. checking bank account balance via the SIM). While the technology has not been updated in the past decade and it’s no longer needed, it’s still present on many SIM cards.
AdaptiveMobile Security has identified mobile operators in over 30 countries providing SIM cards with this technology. The company’s researchers believe up to 1 billion devices could be vulnerable as the Simjacker attack works regardless of which manufacturer they come from. The attack has been tested against phones from Apple, Google, Huawei, Samsung, Motorola and ZTE, and even against some IoT devices that use SIM cards.
It’s worth noting that while some of the commands, such as obtaining a device’s location, don’t require any user interaction and there is no visual evidence of the attack, others, such as making a call, do require some user interaction on mobile phones.
“We believe that the Simjacker attack evolved as a direct replacement for the abilities that were lost to mobile network attackers when operators started to secure their SS7 and Diameter infrastructure,” AdaptiveMobile explained. “But whereas successful SS7 attacks required specific SS7 knowledge (and access), the Simjacker Attack Message require a much broader range of specific SMS , SIM Card, Handset, Sim Toolkit , S@T Browser and SS7 knowledge to craft.”
The company added, “This investment has clearly paid off for the attackers, as they ended up with a method to control any mobile phone in a certain country, all with only a $10 GSM Modem and a target phone number. In short, the advent of Simjacker means that attackers of mobile operators have invested heavily in new attack techniques, and this new investment and skillset means we should expect more of these kinds of complex attacks.”
AdaptiveMobile says it has been working with customer mobile network operators to block attacks and notified both the GSM Association (representing the mobile operator community) and SIMalliance (representing SIM card manufacturers) of the threat.
Related: Many Vulnerabilities Found in Oracle’s Java Card Technology
Related: Stolen SIM Card Keys Could be Powerful Spy Tool
Related: Critical Flaw Exposes Mobile Devices, Networks to Attacks














