New details have emerged about the recent Shamoon 3 attacks, including information on several malware samples, targets in additional sectors, and some links to threat groups believed to be operating out of Iran.
Several new samples of the notorious Shamoon malware emerged recently. While initially researchers could not say who had been targeted, an increasing number of targets have come to light in the past days following the analysis of several cybersecurity firms.
Alphabet-owned Chronicle discovered one sample that had been uploaded to its VirusTotal service from Italy on December 10. It is believed that this variant was used to target Italian oil and gas services company Saipem, which reported that the malware had wiped files from 300-400 servers and up to 100 PCs of a total of roughly 4,000 machines. The company said the attack mainly impacted servers in the Middle East, including Saudi Arabia, the United Arab Emirates and Kuwait, along with some devices in India and Scotland.
One of Saipem’s customers is Saudi Arabian oil giant Saudi Aramco, one of the first victims of Shamoon back in 2012. Shamoon 2 emerged in 2016, when security firms observed more attacks on Saudi Arabia and the Persian Gulf region.
Symantec has now reported seeing Shamoon 3 attacks against an organization in Saudi Arabia and one in the United Arab Emirates. Both targets are in the oil and gas industry and the attacks were detected during the same week as the attack against Saipem.
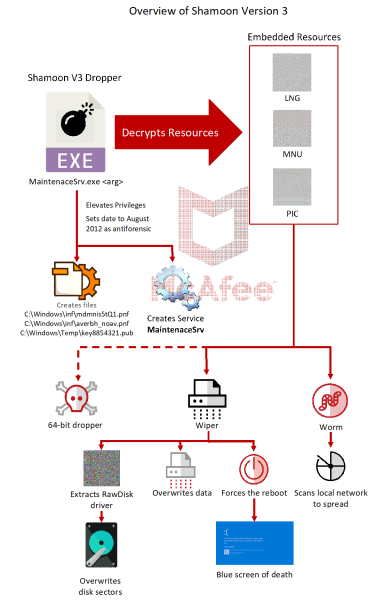
McAfee has reported seeing Shamoon 3 attacks against oil, gas, telecom, energy and government organizations in the Middle East and southern Europe. The company says the latest variant of the wiper is 80 percent similar to version 1 and 28 percent similar to version 2.
Another interesting piece of information shared by Symantec is that the Saudi Arabian organization hit by Shamoon 3 had recently also been targeted by an Iran-linked threat group known as APT33 and Elfin. The same organization also had some systems infected with a piece of malware tracked as Stonedrill, which has been linked by researchers to Shamoon.
“There were additional attacks against this organization in 2018 that may have been related to Elfin or could have been the work of yet another group,” Symantec researchers said in a blog post. “The proximity of the Elfin and the Shamoon attacks against this organization means it is possible that the two incidents are linked.”
Symantec also noted that the latest Shamoon attacks also involved a second wiper, tracked as Filerase, which overwrites files on the infected devices. Some researchers said Shamoon wipes both the infected device’s files and master boot record (MBR), but Symantec claims Shamoon erases the MBR, while Filerase is in charge of destroying files.
Several samples of Shamoon 3 have been identified. The one linked to the Saipem attack had a trigger date of December 7, 2017, which meant that the malware would step into action if the date on the compromised system was set after this day.
However, researchers at Anomali said they also found a sample with a detonation date of December 12, 2017, which, unlike the other sample, was packaged using an open source packer called UPX. This sample was disguised as a VMware Workstation file and it was uploaded to VirusTotal on December 13 by a user in the Netherlands.
“Researchers believe that the detonation dates from 2017 represent attacker efforts to have malware samples detonate immediately upon infection of a victim system. This may be achieved by altering the detonation date to 1 year in the past,” Anomali Labs experts said in a blog post. “Therefore, it is possible that a sample with a detonation date of December 12, 2017 represents a second wave of Shamoon V3 malware that was utilized on December 12, 2018.”















