According to security vendor Incapsula, August was a busy month for Web Application attacks. The company’s latest “attack heat map report” shows some interesting snapshots of the Web, including an overall attack level in Denmark of 0.74 percent, which was launched from a single source.
The attacks in August represent Remote File Inclusion and Local File Inclusion attacks, where an attacker can upload files or call files on an insecure server, directory traversal; which allows an attack the ability to navigate outside of the normal server paths; and targeted attacks against vulnerable software or other applications such as WordPress or something similar.
According to the data taken from 200 million sessions captured by their monitoring network, Incapsula says that 73-percent of all the attacks were classified as takeovers. After that, 11-percent represented Data Theft (SQL Injection), 16-percent were linked Credential Theft (Cross-Site Scripting), and lastly vulnerability scanning.
Location wise, the U.S., followed by China and Russia, generated the highest volume of attack traffic. Target wise, the U.K. was the top target, followed by Denmark and the U.S.
The image below has the full breakdown, with a description of the attack types used included below.
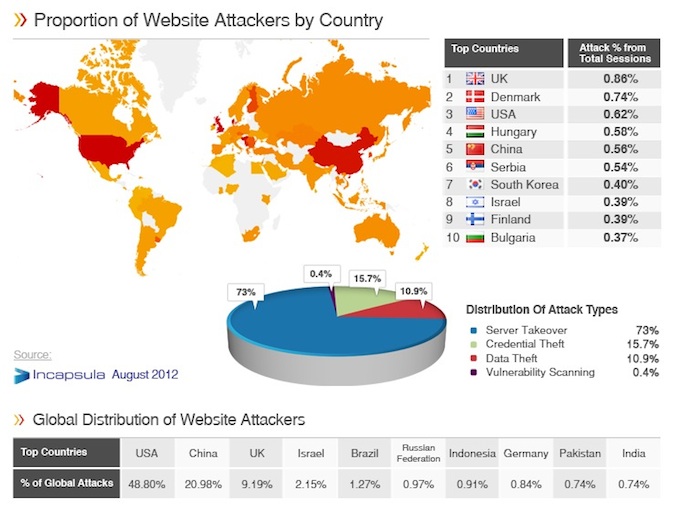
Attack Types
Server Takeover: Includes Remote File Inclusion, Local File Inclusion, Directory Traversal and specific known web applications or web server vulnerabilities. These security risks are the most widespread due to their effectiveness but moreover because they are very easy to automate. These attacks are mainly used for web server takeover. By taking over the web server, a hacker can plant malicious code in the site’s code, deface the site or even use the web server as a bot for attacking other sites.
Data Theft: Attacks that are targeting databases which are used in most common web applications. This weakness happens when a web application does not properly sanitize user input and allows the attacker to affect the SQL statements that are executed by the database. This attack is mostly used for stealing sensitive data – bypassing authentication or even causing a Denial of Service.
Credentials Theft: Cross Site Scripting – XSS in short, is a method in which a hacker uses a weakness in the web application which allows the attacker to execute malicious code in the user’s browser. This attack can be used to steal user credentials, alter the site’s appearance or even redirect the user to sites that are hosting malware.
Vulnerability Scanning: Vulnerability scanners are tools which scan web applications to find security vulnerabilities. Some of them are commercial tools (as Nessus, Qualys, Acunetix & WhiteHat security) used by website owners to self-check their websites for security breaches, and some are self-developed by hackers, which use them to find security vulnerabilities on websites and then exploit these vulnerabilities for targeted attacks .















