A newly observed botnet capable of self-replicating and self-propagation is targeting multiple Internet of Things (IoT) vulnerabilities for initial access, cybersecurity solutions provider Fortinet warns.
Dubbed Zerobot, the malware is written in the Golang (Go) programming language and has several modules for self-replication, self-propagation, and for conducting attacks on different protocols.
The malware has been observed communicating with its command-and-control (C&C) server via the WebSocket protocol and targeting twelve architectures, including i386, amd64, arm64, arm, mips, mipsle, mips64, mips64le, ppc64, ppc64le, riscv64, and s390x.
To date, Fortinet has identified two variants of the botnet, one containing basic functions and used before November 24, and another that can replicate itself and target more endpoints, which has been distributed since mid-November.
The malware includes 21 exploits, including code targeting recent Spring4Shell and F5 Big-IP flaws, other known vulnerabilities, and various security defects in IoT devices such as routers, surveillance cameras, and firewalls.
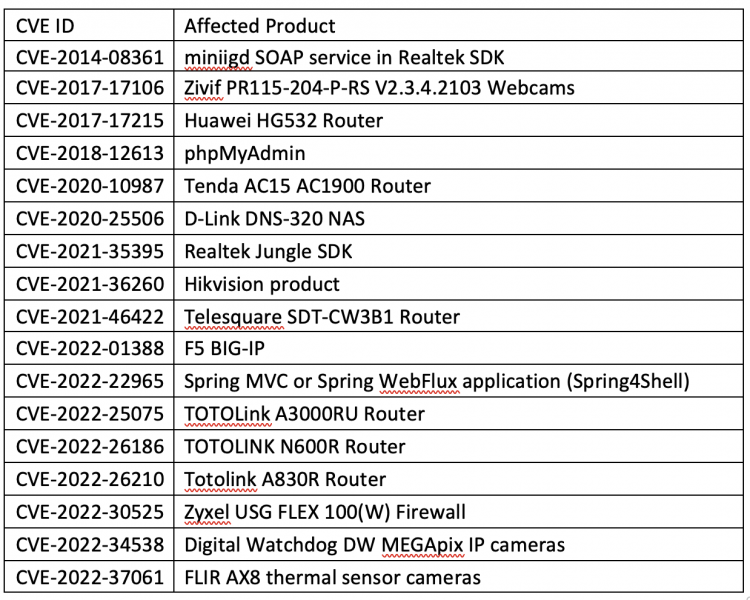
Zerobot also includes two exploits taken from a website that claims to share vulnerabilities for educational purposes.
Once a device has been compromised, Zerobot copies itself to the system, sets up a module to prevent users from disrupting its operation, after which it initializes connection to the C&C, sending a JSON file containing victim information, and then waits for commands from the server.
Based on received commands, the malware keeps the connection alive, launches/stops attacks on different protocols, updates and restarts itself, scans for open ports and begins spreading itself, runs commands, or kills its process.
“[Zerobot] first appeared on November 18 and is designed to target a variety of vulnerabilities. Within a very short time, it was updated with string obfuscation, a copy file module, and a propagation exploit module that makes it harder to detect and gives it a higher capability to infect more devices,” Fortinet says.
Organizations are advised to review the list of targeted vulnerabilities and apply available patches as soon as possible.
Related: Multi-Purpose Botnet and Infostealer ‘Aurora’ Rising to Fame
Related: Russia-Linked Cyclops Blink Botnet Attacking ASUS Routers
Related: New ‘Enemybot’ DDoS Botnet Targets Routers, Web Servers













