IT security professionals, particularly executives, often access information that is not relevant to their day-to-day work, according to a new One Identity study focusing on “snooping” on the corporate network.
Dimensional Research polled more than 900 IT security professionals on behalf of One Identity. The respondents were from various types of companies in the United States, the United Kingdom, Germany, France, Australia, Singapore and Hong Kong, with at least 500 employees.
When asked if their company’s employees ever attempt to access information that is not necessary for their day-to-day work, 92% admitted it happens and 23% said it happens frequently. There are no major differences based on region or the size of the company.
Roughly two-thirds of the IT security pros that took part in the survey admitted snooping themselves, although 51% claim they do it rarely. Professionals from the U.S. seem to snoop the least (50%) while ones in Germany snoop the most (80%).
Interestingly, executives appear to be the guiltiest (71% said they snoop), followed by managers (68%) and other members of the IT security team (56%).
Globally, one in three IT security professionals who took part in the survey said they had accessed sensitive information about their company’s performance, despite not being required to do so as part of their job. This behavior can be seen more in Europe and Asia, and less in the U.S. and Australia, the report shows.
Again, executives and managers are more likely to look at company performance data compared to non-managers.
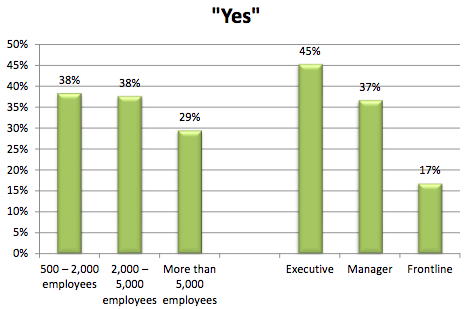
The survey also found that cybersecurity professionals working in the technology sector are most likely to look for data on their organization’s performance.
“While insider threats tend to be non-malicious in intent, our research depicts a widespread, intrusive meddling from employees when it comes to information that falls outside their responsibility — and it could be that meddling that ends up putting their employers in hot water,” explained John Milburn, president and general manager of One Identity.
“Without proper governance of access permissions and rights, organizations give employees free reign to move about the enterprise and access sensitive information like financial performance data, confidential customer documentation, or a CEO’s personal files. If that information winds up in the wrong hands, corporate data loss, customer data exposure or compliance violations are possible risks that could result in irreversible damage to the business’s reputation or financial standing,” Milburn added.
Related: Psycho-Analytics Could Aid Insider Threat Detection
Related: Alarming Percentage of Employees Hide Security Incidents
















