Incidents of data breaches continue to be on the rise. The increase was so great in 2013—62 percent – that Symantec coined it the year of the mega breach. And it isn’t just server side breaches like Target, Home Depot and JP Morgan Chase that are grabbing the headlines. The Impact of Mobile Devices on Information Security: A Survey of IT Professionals, found (PDF) that 79% of companies reported a mobile data breach, with the cost of data loss ranging from less than $10K to over $500K per incident, proving that mobile security needs to be a priority within enterprises.
If you can’t trust the security of operating systems on laptops, you certainly can’t trust operating systems on mobile devices to keep corporate information safe. Often times, enterprises simply rely on iOS or Android operating systems to ensure mobile data security, which doesn’t work. When it comes to mobile security, enterprises need to shift from a single layer to a multi-layer defense strategy, with the focus on applications and the data within them, not the user or the device. The truth is while legitimate mobile apps can be “safe,” many more are risky. However, there is hope. In fact, there are several ways to identify a “risky” app.
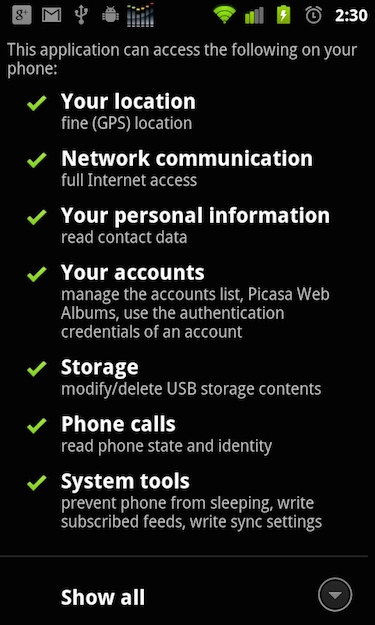 Mobile applications can pose serious risk to enterprise data, customers and security in general, so it is especially important for organizations to be able to identify these apps.
Mobile applications can pose serious risk to enterprise data, customers and security in general, so it is especially important for organizations to be able to identify these apps.
The first step is to determine if the application is genuine in intention or malicious. It’s difficult to establish the threat without knowing the application’s intent. Moreover, mobile malware is often a lesser threat than insecurities in legitimate applications. As such, when identifying risky apps, we must also look at the legitimate applications that have good intent, but may not be as secure as we need them to be.
A few characteristics of mobile apps that should be evaluated are as follows: the security posture of the application, how the application handles data storage, how or if the application writes to disk, if data (especially sensitive or PIIA data) is encrypted, and how long data resides on the device or if it purges data after it’s utilized.
In addition, no mobile app is an island. Enterprises also have to think about how applications interact with other applications. Is there a way for other applications, legitimate or not, to compromise the security of this application? For instance, does an application really need to have access to your text messages?
When downloading an application, users are prompted to allow applications to access information on devices such as contacts, text messages, calendars and more. If an application has access to your text messages, does that reduce the effectiveness of security tools such as two-factor authentication, thus creating more risk for the enterprise and the end user?
Along the same lines as permissions, enterprises need to worry about mobile functionality and what a user may do intentionally or unintentionally with corporate data. Although permissions within functionality are not security flaws per se, they can increase the risk to the enterprise. When determining how risky an app is, we must consider intentional features within these permissions to determine whether or not they’re a risk to the enterprise. When evaluating risky apps, enterprises need to know not only how data is stored, but also how it’s transmitted across the network and whether an app is properly verifying the https connection and preventing man-in-the-middle attacks.
Once the application has been examined and the impact to security has been evaluated, enterprises must determine a course of action. The traditional security strategy is to lock down application access and block users from accessing and utilizing any application that the enterprise deems risky, even if the apps are legitimate and increase productivity. As I’ve seen time and time again as a former CISO, this tactic just doesn’t work.
As with desktops, when CISOs try to remove risky applications, employees simply find workarounds to access applications and software that increase productivity. BYOD enables users to deploy their own applications, therefore blocking apps has become even less effective.
So in today’s fast paced mobile environment, how do security professionals manage risky mobile apps without exposing the company to unnecessary risk while supporting productivity? Now, we must turn our focus to protecting the data and fortifying applications to ensure that we can trust the applications that users use.














