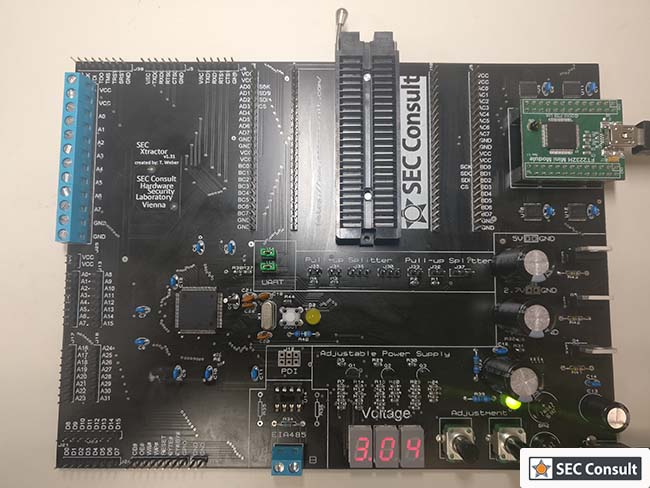
Austria-based IT security services and consulting company SEC Consult on Wednesday announced the release as open source of its SEC Xtractor assisted hardware analysis tool.
SEC Xtractor, which SEC Consult has used for several research and customer projects in the past years, started off as a memory extraction and UART (Universal Asynchronous Receiver/Transmitter) interface project. It was built after the company determined that none of the existing hardware analysis tools met all its requirements.
SEC Xtractor has now become a tool that allows researchers to dump the content of NAND, NOR, SPI and I2C flash memory without the need for soldering, as long as the chip has been removed from the targeted device. The system can also act as a UART-to-USB converter and a JTAG adapter.
SEC Xtractor was developed in C and its capabilities can be easily extended, SEC Consult said.
The company told SecurityWeek that the price of the hardware components needed to build the tool is roughly €100-130 ($110-145), depending on shipping costs.
SEC Xtractor has been released as open source to aid hackers, but SEC Consult does not exclude the possibility to offer it as a commercial product at one point if it finds the right collaborator.
SEC Consult will continue to maintain the tool, but it welcomes contributions. All the information needed to build the hardware analysis tool is available on GitHub.
Related: Cruise Releases Automated Firmware Security Analyzer to Open Source
Related: FireEye Releases Open Source Persistence Toolkit ‘SharPersist’
Related: Cloudflare Open-Sources Network Vulnerability Scanner
Related: Sophos Makes Sandboxie Free in Transition to Open Source











