
SINGAPORE — SECURITYWEEK 2019 ICS CYBER SECURITY CONFERENCE — Some of the pieces of digital evidence that led to security researchers linking the notorious Triton malware to a Russian research institute were removed after the information was made public.
A blog post published in October 2018 by cybersecurity firm FireEye assessed with “high confidence” that the Triton malware, also known as Trisis and HatMan, was linked to Russia, specifically the Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM), a technical research organization located in Moscow and owned by the Russian government.
FireEye, which tracks this activity as TEMP.Veles, analyzed some of the Triton-associated tools uploaded to online malware analysis services and stumbled upon a path that led researchers to the online moniker of a Moscow-based individual who had been involved in vulnerability research and who had apparently been a professor at CNIIHM.
However, a few weeks after FireEye published its attribution report, the company noticed that some of the evidence had started disappearing from the internet, Yihao Lim, senior cyber threat intelligence analyst at FireEye, said on Wednesday at SecurityWeek’s ICS Cyber Security Conference in Singapore.
Nathan Brubaker, who leads the FireEye Intelligence Cyber-Physical team, told SecurityWeek that within 2-4 weeks of FireEye’s blog post being published they noticed that CNIIHM had removed many photos from its website, including one showing the individual who allowed them to make the connection between Triton and the institute.
Brubaker said they also noticed that some information related to the department the individual worked in was also altered.
Furthermore, registrant (WHOIS) data associated with an IP address range used by the institute had been masked a little over two weeks after FireEye’s blog post was published — it initially clearly showed that the IP range belonged to CNIIHM, but all references to CNIIHM were later removed. FireEye had seen one of these IPs doing network reconnaissance against critical infrastructure organizations and it had been involved in other malicious activity supporting TEMP.Veles.
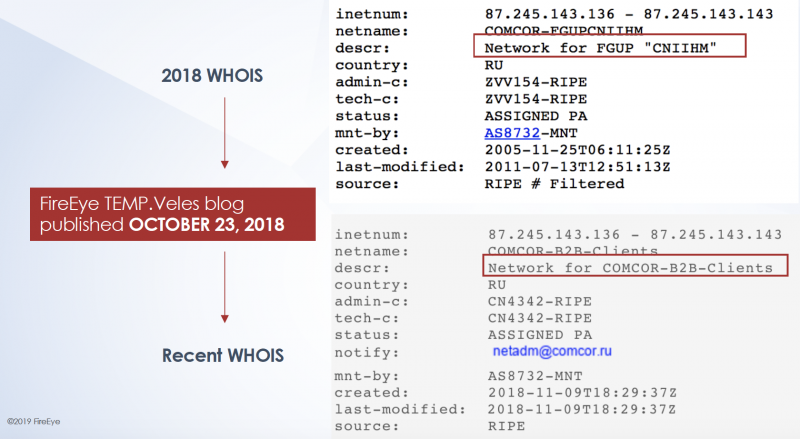
The cybersecurity firm has not made public all the evidence that led it to conclude that CNIIHM has contributed to the development of the Triton framework, but it has disclosed several of the clues it has found. FireEye has highlighted that it does not claim the entire Triton framework is the work of this organization.
It pointed out that CNIIHM’s knowledge and personnel would make it highly capable of developing the Triton malware. It has research departments that specialize in the protection of critical infrastructure and the development of weapons and military equipment, and it collaborates with a wide range of other organizations, including ones involved in computer science, electrical engineering, defense systems, and information technologies.
When it published its attribution report, FireEye mentioned that while it’s possible some CNIIHM employees conducted these activities without the knowledge of the organization, this scenario is unlikely considering that the activity spans several years. The apparent clean-up effort seems to reinforce CNIIHM’s involvement.
The existence of Triton came to light in 2017 after the malware triggered a Schneider Electric safety system and caused disruptions at an oil and gas plant in Saudi Arabia. FireEye’s Mandiant was called in to investigate the incident and the company said it recently responded to another attack carried out by the Triton group against a critical infrastructure facility. However, it could not share any information about the target of this second attack, but it did clarify that the actual Triton malware was not observed in the operation.
The security firm recently published more details on the techniques and tools used by the Triton attackers and noted that the group focused on maintaining access, moving laterally, conducting reconnaissance, and avoiding being detected, rather than stealing information from compromised devices.
Industrial cybersecurity firm Dragos, which tracks the group behind Triton as Xenotime, reported last year that the hackers had expanded their list of targets to outside the Middle East and had started targeting a wider range of safety systems.
Related: Industry Reactions to New Triton Attacks on Critical Infrastructure













