Threat hunters at Mandiant are shining the spotlight on a pair of previously undocumented operational technology (OT) attacks last October by Russia’s “Sandworm” hackers that caused an unplanned power outage and coincided with mass missile strikes on critical infrastructure across Ukraine.
The attacks, which spanned several months and culminated in two disruptive events on October 10 and 12 last year, leveraged what Mandiant is describing as a “novel technique” for impacting industrial control systems (ICS) and OT.
Mandiant said it caught Sandworm executing code within an end-of-life MicroSCADA control system and issuing commands that impacted the victim’s connected substations.
MicroSCADA, a Hitachi Energy product, is deployed in more than 10,000 substations, managing and monitoring power across critical infrastructure such as power grids, process industries, hospitals, seaports, and data centers.
“The actor first used OT-level living off the land (LotL) techniques to likely trip the victim’s substation circuit breakers, causing an unplanned power outage that coincided with mass missile strikes on critical infrastructure across Ukraine,” Mandiant said in a technical paper with details on the attacks.
Just two days after the OT attack, the Russian hackers conducted a second disruptive event by deploying a new variant of CADDYWIPER in the victim’s IT environment to cause additional damage and potentially to “remove forensic artifacts.”
“This attack represents the latest evolution in Russia’s cyber physical attack capability,” the company warned, noting a “growing maturity of Russia’s offensive OT arsenal that includes the ability to pinpoint novel OT threat vectors, develop new capabilities, and leverage different types of OT infrastructure to execute attacks.
The Sandworm hacking team, caught several times carrying out espionage, influence and malware attack operations in support of Russia’s Main Intelligence Directorate (GRU), appears to have developed the OT component of the attack in as little as two months, Mandiant said.
“This indicates that the threat actor is likely capable of quickly developing similar capabilities against other OT systems from different original equipment manufacturers (OEMs) leveraged across the world,” the company said.
It’s unclear how the hackers gained initial access to the organization’s systems. They were first seen in the target’s environment in June 2022, when they deployed a webshell on an internet-exposed system.
For the OT side of the attack, Sandworm deployed an ISO image file as a virtual CD-ROM in a hypervisor that hosted the MicroSCADA supervisory control and data acquisition (SCADA) instance for the target’s substation environment. This ISO contained files that executed ‘scilc.exe’, a legitimate MicroSCADA utility that enabled the attackers to run arbitrary commands.
While Mandiant was unable to determine exactly which commands were executed by the attackers, they likely attempted to open circuit breakers. The MicroSCADA server would have relayed the commands to substation remote terminal units (RTUs) via either the IEC-60870-5-101 protocol for serial connections or the IEC-60870-5-104 protocol for TCP/IP connections.
Mandiant believes the threat actor had access to the SCADA system for as much as three months.
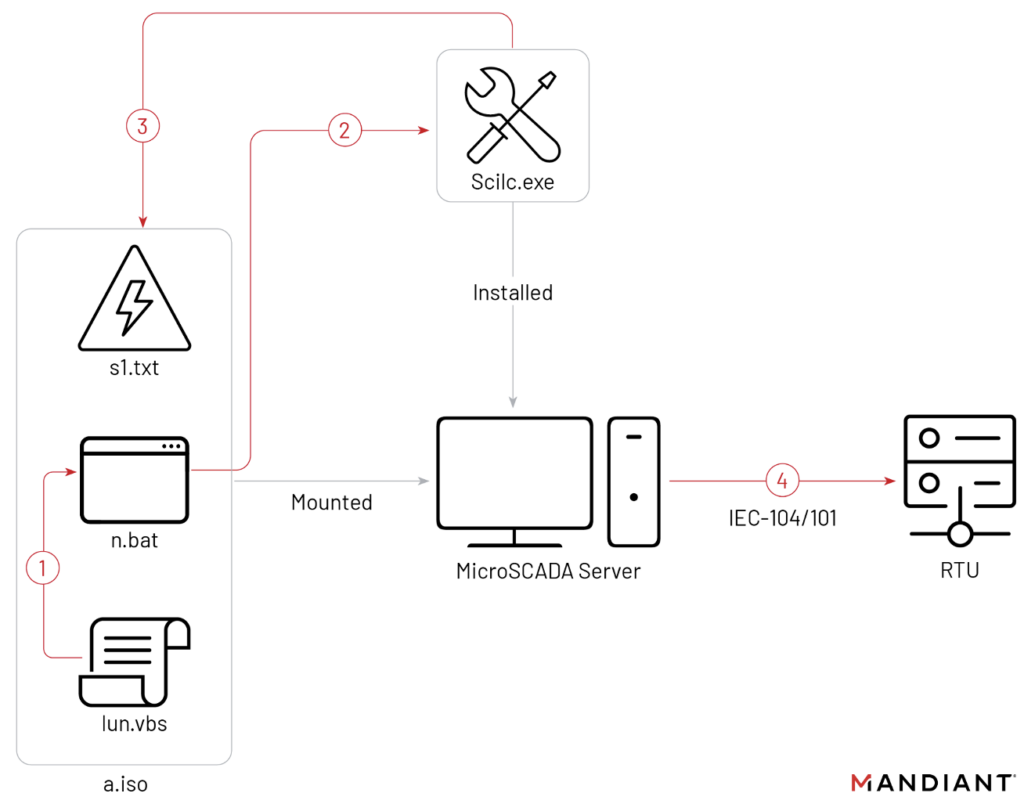
The Mandiant team said the intricacies of the attack show the Russian hackers are moving quickly to streamline OT attack capabilities through simplified deployment features and cautioned that Sandworm’s use of Living off the Land binary (LotLBin) to disrupt an OT environment “shows a significant shift in techniques.”
Speaking to SecurityWeek on background, a member of the research outfit warned that so-called ‘living off the land’ in OT is a new class of attack that should worry defenders at critical infrastructure installations.
“Given Sandworm’s global threat activity and novel OT capabilities, we urge OT asset owners to take action to mitigate this threat,” Mandiant said. In its report, the security firm shared a range of detections, hunting and hardening guidance, and MITRE ATT&CK mappings.
Russia has used OT malware such as Industroyer and Industroyer2 in previous attacks targeting Ukraine’s energy sector.
Mandiant’s researchers are expected to share additional details on the destructive October attacks at the CYBERWARCON event in Washington, DC on Thursday.
Related: New Russia-Linked CosmicEnergy ICS Malware Could Disrupt Electric Grids
Related: Sandworm Hackers Hit French Monitoring Software Vendor Centreon
Related: Five Eyes: Russian Malware Targeting Ukrainian Military Android Devices
Related: Leaked Documents Detail Russia’s Cyberwarfare, OT Attack Tools
















