Over the past year, a Russian cybercrime group has launched over 200 business email compromise (BEC) campaigns targeting multinational organizations.
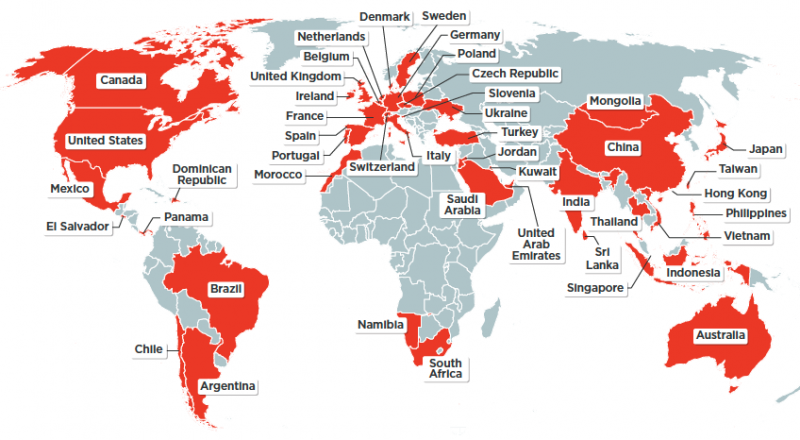
Referred to as Cosmic Lynx, the threat actor has targeted individuals in 46 countries on six continents, nearly all of whom were employees of Fortune 500 or Global 2000 companies.
“Even employees in countries not typically seen in phishing campaign targeting sets, like Namibia and Mongolia, were targeted by Cosmic Lynx,” email security company Agari explains in a new report.
The group mainly focused on senior-level executives, with three quarters of the targets holding titles such as managing director, vice president, or general manager. Other targeted positions include subsidiary or country-level CEO, president, and CFO.
As part of their attacks, the hackers use a dual impersonation scheme. Impersonating a company’s CEO, the group asks the targeted employee to coordinate payments for the acquisition of an Asian company. Additionally, they hijack the identity of an attorney at a legitimate law firm in the UK, and leverage it to facilitate the fake acquisition.
The stolen funds are mainly sent to mule accounts in Hong Kong, but the threat actor has also used secondary accounts in Hungary, Portugal, and Romania. However, the group appears to avoid using secondary mule accounts in the United States.
Unlike other BEC fraudsters who typically ask for an average amount of $55,000 to be wired to mule accounts, Cosmic Lynx asks for hundreds of thousands or even millions of dollars, Agari points out.
Cosmic Lynx is aware of an organization’s use of DMARC. While it typically directly spoofs CEO email addresses, the group attempts to circumvent DMARC policies by adding the CEO’s email address to the display name, so that it would seem the email was sent from the CEO’s account.
The adversary was also observed taking advantage of the COVID-19 pandemic starting late March, by using crisis-related themes at the beginning of the initial email sent to the targeted executive. By late May, the hackers started referencing the reopening of global economies in their introductory emails.
Domains employed across campaigns mimic secure infrastructure (such as secure-mail-gateway[.]cc, mx-secure-net[.]com, etc.) and mailboxes typically reference celestial bodies (including “smtp-mars,” “tls-sirius,” or “gateway-mercury,” among others).
The group has used the bulletproof hosting provider NiceVPS to register some of the domains, Agari security researchers discovered. Furthermore, they were able to link the Cosmic Lynx infrastructure with banking Trojans Emotet and Trickbot, but also with Android click fraud, a known carding portal, and Russian fake document websites.
Agari was able to piece together evidence suggesting that the group is of Russian origin, including email metadata, working hours, and infrastructure information, but notes that solid attribution is not yet possible.
“Evidence that more sophisticated threat groups are adding BEC to their attack repertoire should concern everyone. Unlike traditional BEC groups, Cosmic Lynx has demonstrated the capability to develop much more complex and creative attacks that sets them apart from other more generic BEC attacks we see every day,” Agari concludes.
Related: Microsoft Files Lawsuit to Seize Fake Domains Used in COVID-19-Themed BEC Attacks
Related: Nigerian Instagram Star Extradited to U.S. Over Role in Cybercrime Schemes















